New Citrix 1Y0-A22 dumps exam questions and answers free download from leads4pass. Best useful Citrix 1Y0-A22 dumps pdf files and vce youtube demo update free shared. “Citrix XenApp 6.5 Advanced Administration” is the name of Citrix https://www.leads4pass.com/1y0-a22.html exam dumps which covers all the knowledge points of the real Citrix exam. Latest Citrix 1Y0-A22 dumps pdf training materials and study guides free update, pass Citrix 1Y0-A22 exam test easily at first try.
Useful latest Citrix 1Y0-A22 dumps pdf practice files: https://drive.google.com/open?id=0B_7qiYkH83VRYmR4UXRyVEhlX0U
Useful latest Citrix 1Y0-A26 dumps pdf practice files: https://drive.google.com/open?id=0B_7qiYkH83VRVTY2VzE4YnR4bUE

QUESTION 1
An administrator needs to validate the data store in a XenApp farm.
The administrator should use the DSCHECK command with the /CLEAN parameter after _______. (Choose the correct option to complete the sentence.)
A. restoring the data store
B. backing up the data store
C. restarting the XenApp server
D. restarting the IMA Service on the data collector
Correct Answer: B
QUESTION 2
Scenario: An administrator in a XenApp farm is in the process of replacing a couple of the failed XenApp servers in the farm. The administrator has been instructed to execute the DSCHECK command once the servers have been replaced.
What will be the outcome of executing the DSCHECK command?
A. Recover the local data store
B. Purge corrupt local host cache entries
C. Purge the data store of incorrect entries
D. Display information about servers in the farm
Correct Answer: C
QUESTION 3
Scenario: An administrator migrated the data store of a Citrix XenApp 6.5 server farm from Microsoft SQL Server Express on XenApp server XAS01 to a separate Microsoft SQL Server 2008 cluster.
The administrator tested the move, noted that the cluster is running well and found no errors. None of the XenApp 6.5 servers can connect to the new location of the data store.
In this scenario, when should the administrator use the DSCHECK command?
A. After restarting the data collector
B. After using the DSMAINT command
C. After running the QFARM command
D. After using the CHANGE CLIENT command
Correct Answer: B
QUESTION 4
When should an administrator use the DSCHECK command line utility?
A. To fix errors on server entries in the data store
B. To fix errors related to configuring Proxy Authentication
C. To fix errors in the local host cache on each XenApp 6.5 server
D. To generate a report of logon/logoff activity for a XenApp 6.5 server
Correct Answer: A
QUESTION 5
Scenario: An administrator has configured a XenApp Web site and customized the footer text of the site to reflect the required customer-specific hyperlinks. 1Y0-A22 dumps The administrator now plans to back up the site.
Which file must the administrator back up?
A. Default.ica
B. Web.config
C. Repair.SFO
D. WebInterface.conf
E. LoginMainFormFoot.inc
Correct Answer: D
QUESTION 6
After repairing a XenApp Web site, an administrator notices that the customized footer text is missing.
Which file must the administrator restore from backup?
A. Default.ica
B. Web.config
C. Repair.SFO
D. WebInterface.conf
E. LoginMainFormFoot.inc
Correct Answer: D
QUESTION 7
Scenario: An administrator used the Server Configuration Tool to install a Microsoft SQL Server Express data store database automatically as part of a XenApp 6.5 farm installation. The initial configuration consisted of a single zone and servers in a single physical location. The administrator added an equal number of servers and users to the farm at a second physical location over a WAN.
Which action would require the administrator to migrate the data store database from Microsoft SQL Server Express to Microsoft SQL Server?
A. Adding an additional zone to the farm
B. Replicating the data store to a second database server
C. Moving the data store from local storage to SAN storage
D. Adding the configuration logging database to the same SQL server
Correct Answer: B
QUESTION 8
Scenario: An administrator used the Server Configuration Tool to install a Microsoft SQL Server Express data store database automatically as part of a XenApp 6.5 farm installation. The initial configuration consisted of a single zone and servers in a single physical location. The administrator added an equal number of servers and users to the farm at a second physical location over a WAN.
Which action would require the administrator to migrate the data store database from Microsoft SQL Server Express to Microsoft SQL Server?
A. Adding an additional zone to the farm
B. Mirroring the SQL database to a second SQL server
C. Moving the database from local storage to SAN storage
D. Adding the configuration logging database to the same SQL server
Correct Answer: B
QUESTION 9
Scenario: An administrator used the Server Configuration Tool to install a Microsoft SQL Server Express data store database automatically as part of a XenApp 6.5 farm installation. The initial configuration consisted of a single zone and servers in a single physical location. The administrator added an equal number of servers and users to the farm at a second physical location over a WAN.
Which new requirement would require the administrator to migrate the data store database from Microsoft SQL Server Express to Microsoft SQL Server?
A. Implementing database mirroring
B. Adding an additional zone to the farm
C. Moving the database from local storage to SAN storage
D. Adding the configuration logging database to the same SQL server
Correct Answer: A
QUESTION 10
Scenario: A XenApp Administrator in an enterprise environment plans to use Access Gateway to secure ICA connections from the external network. The Access Gateway is in the DMZ using ICA proxy mode.
Which two locations for these components would be the most secure? (Choose two.)
A. Place the XML broker in the DMZ.
B. Place the Web Interface in the DMZ.
C. Place the XML broker in the internal network.
D. Place the Web Interface in the internal network.
Correct Answer: CD
QUESTION 11
Scenario: A XenApp Administrator in a small environment plans to use Access Gateway to secure ICA connections from an external network. 1Y0-A22 dumps The Access Gateway is in the DMZ in ICA proxy mode. The environment requires minimum configuration to secure connections from the Web Interface server to the XML broker server.
Where should the administrator place the Web Interface server and XML broker?
A. On one server and place the server in the DMZ
B. On separate servers and place the servers in the DMZ
C. On one server and place the server in the internal network
D. On separate servers and place the servers in the internal network
Correct Answer: C
QUESTION 12
In order for the Web Interface server to correctly work with the Access Gateway Enterprise Edition configuration in the attached exhibit,
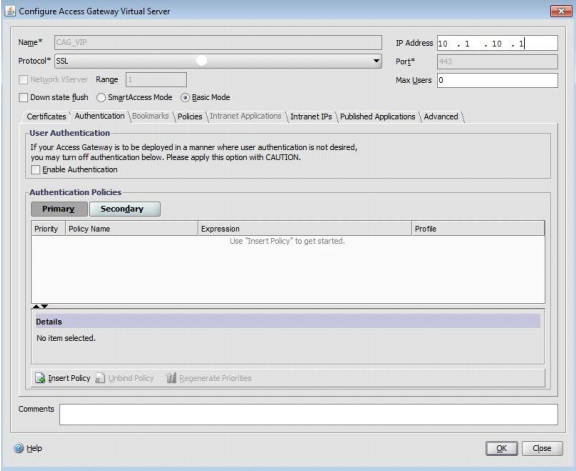
the administrator must configure the authentication point at __________. (Choose the correct option to complete the sentence.)
A. LDAP
B. RADIUS
C. the Web Interface
D. the Access Gateway
Correct Answer: C
QUESTION 13
Which two methods can an administrator use to configure Web Interface in high availability mode? 1Y0-A22 dumps (Choose two.)
A. Windows Cluster services
B. NetScaler Load Balancing feature
C. Windows Load Balancing services
D. NetScaler Access Gateway feature
Correct Answer: BC
QUESTION 14
A XenApp Administrator plans to use Citrix NetScaler to load balance Web Interface servers.
Which persistence setting should the administrator choose to correctly configure high availability for Web Interface?
A. NOCE
B. DESTIP
C. SOURCEIP
D. COOKIEINSERT
Correct Answer: D
QUESTION 15
Scenario: A XenApp Administrator of a 100-server farm needs to apply Citrix and vendor hotfixes on a monthly basis, and a server restart is always required. The administrator needs to automate this process but does NOT have a third party tool available.
Which two tasks should the administrator complete to guarantee that updates will be applied successfully? (Choose two.)
A. Prohibit logons and notify users.
B. Restart the server and install hotfixes.
C. Apply application load evaluators and notify users.
D. Log off all users from servers and schedule a .EXE setup file installation.
Correct Answer: AB
QUESTION 16
Scenario: The Citrix Administrator of a large farm needs to perform a health check after a scheduled update window. The health check should alert the administrator when the server is unavailable to users.
Which action must the administrator take to perform a health check after a scheduled update window?
A. Use PowerShell SDK scripts to verify the applied updates.
B. Use MFCOM to check applied updates and enabled logons.
C. Use MFCOM scripts to verify enabled logons and open Citrix ports.
D. Use PowerShell SDK scripts to check enabled logons and open Citrix ports.
Correct Answer: D
QUESTION 17
Scenario: A new administrator has been asked to ensure that all servers meet the minimum required patching level. A test server has been used to confirm that all patches can be deployed to the production servers. Testing has identified that production servers are NOT at the same patch level.
Which action can the administrator take to identify which patches are required on each production server?
A. Use the Citrix Computer policy wizard.
B. Use the Citrix AppCenter History node.
C. Use the Citrix AppCenter Configuration Tools node.
D. Use the Prepare this server for imaging and provisioning task.
Correct Answer: C
QUESTION 18
Scenario: A XenApp Administrator needs to deploy a small MSI package across all XenApp servers. This package requires a restart which needs to be scheduled to ensure that all servers do NOT restart at once. 1Y0-A22 dumps
Which action must the administrator take to fulfill the requirement?
A. Set up Installation Manager.
B. Configure Health Monitoring and Recovery.
C. Create a maintenance policy in the AppCenter console.
D. Use the XenApp Server Role Manager to install Installation Manager.
Correct Answer: A
QUESTION 19
Which component should an administrator monitor to verify if the XenApp servers are accepting ICA connections?
A. ICA Listener
B. Logon Monitor
C. Citrix IMA Service
D. Citrix Streaming Service
Correct Answer: A
QUESTION 20
Scenario: Some users in remote offices complain that Citrix sessions are slow, and the network administrator has asked the Citrix Administrator to determine whether any data transmission errors are occurring for a group of sample users. In this environment, EdgeSight, Branch Repeater and Session Reliability are NOT used.
How can the Citrix Administrator determine the extent of data transmission errors based on the sample users?
A. Configure Multi-Stream for sample users.
B. Open the Citrix Connection Center for sample users.
C. Enable ICA round trip calculators for idle connections for sample users.
D. Change the active session limit to something other than Never in the ICA-TCP settings.
Correct Answer: B
The best and most updated Citrix 1Y0-A22 dumps exam practice materials in PDF format download to have a free try. High quality Citrix Popular Exams5 https://www.leads4pass.com/1y0-a22.html dumps pdf training resources which are the best for clearing 1Y0-A22 exam test, and to get certified by Citrix home Popular Exams5. 100% success and guarantee to pass.
High quality Citrix 1Y0-A22 dumps vce youtube: https://youtu.be/l47UGwEjKLA