Leads4Pass 300-725 dumps were updated in October 2024, containing 60 latest exam questions and answers. Candidates can download confidently, which will 100% help pass the Cisco 300-725 SWSA exam.

The new 300-725 dumps will be updated at any time according to the actual situation to ensure real-time effectiveness. Download Leads4Pass 300-725 dumps: https://www.leads4pass.com/300-725.html, free updates for 365 days.
What’s more! You can enjoy online practice tests for free now and make sure you are satisfied before choosing.
Enjoy two Cisco 300-725 SWSA online practice opportunities
| First | Number of exam questions | Second | Related certifications |
| Practice the latest Cisco 300-725 exam materials below | 15 | Leads4Pass 300-725 Online | CCNP Security |
Question 1:
DRAG DROP
Drag and drop the Cisco WSA access policy elements from the left into the order in which they are processed on the right.
Select and Place:
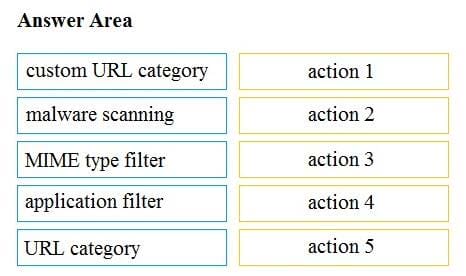
Correct Answer:
Question 2:
What is the benefit of integrating Cisco WSA with TrustSec in ISE?
A. The policy trace tool can be used to match access policies using specific SGT
B. Traffic of authenticated users who use 802.1x can be tagged with SGT to identify profiles in a Cisco WSA
C. ISE can block authentication for users who generate multiple sessions using suspect TCP ports
D. Users in a specific SGT can be denied access to certain social websites.
Correct Answer: D
Question 3:
Which two benefits does AMP provide compared to the other scanning engines on the Cisco WSA? (Choose two.)
A. protection against malware
B. protection against zero-day attacks
C. protection against spam
D. protection against viruses
E. protection against targeted file-based attacks
Correct Answer: AB
Question 4:
Which statement about Cisco Advanced Web Security Reporting integration is true?
A. AWSR uses IP addresses to differentiate Cisco WSA deployments
B. AWSR does not require a license to index data
C. AWSR can remove log files after they are indexed
D. AWSR installation is CLI-based on Windows and Red Hat Linux systems
Correct Answer: D
Question 5:
A network administrator noticed that all traffic that is redirected to the Cisco WSA from the Cisco ASA firewall cannot get to the Internet in a Transparent proxy environment using WCCP. Which troubleshooting action must be taken on the CLI to make sure that WCCP communication is not failing?
A. Disable WCCP to see if the WCCP service is causing the issue
B. Explicitly point the browser to the proxy
C. Ping the WCCP device
D. Check WCCP logs in debug mode
Correct Answer: D
Question 6:
What is the function of a PAC file on a Cisco WSA?
A. The file allows redirection of web traffic to a specific proxy server
B. The file is mandatory for a transparent proxy to redirect user traffic
C. The file provides instructions about which URL categories are permitted
D. The file is mandatory for an explicit proxy to forward user traffic
Correct Answer: A
Question 7:
Which method is used by AMP against zero-day and targeted file-based attacks?
A. analyzing the behavior of all files that are not yet known to the reputation service
B. periodically evaluating emerging threats as new information becomes available
C. implementing security group tags
D. obtaining the reputation of known files
Correct Answer: D
Question 8:
Which two caching modes are available in the Cisco WSA? (Choose two.)
A. active cache
B. all cache
C. aggressive cache
D. safe cache
E. no-cache
Correct Answer: CD
Question 9:
Which information in the HTTP request is used to determine if it is subject to the referrer exceptions feature in the Cisco WSA?
A. protocol
B. version
C. header
D. payload
Correct Answer: C
Requests for embedded content usually include the address of the site from which the request originated (this is known as the “referer” field in the request\’s HTTP header). This header information is used to determine the categorization of the referred content.
Question 10:

Refer to the exhibit. Which command displays this output?
A. grep
B. log config
C. rollover now
D. tail
Correct Answer: A
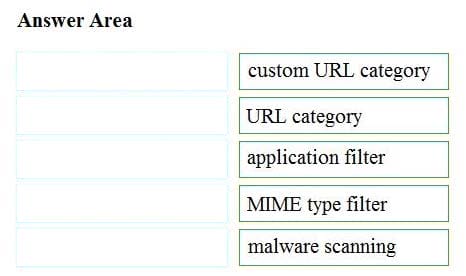
Question 11:
DRAG DROP
Drag and drop the properties from the left onto the correct advanced web proxy setting descriptions on the right.
Select and Place:

Correct Answer:
Question 12:
Which certificate format does a Cisco WSA need when an HTTPS proxy is configured?
A. DER
B. CER
C. PEM
D. CRL
Correct Answer: C
Question 13:
Which key is needed to pair a Cisco WSA and Cisco ScanCenter for CTA?
A. public SSH key that the Cisco WSA generates
B. public SSH key that Cisco ScanCenter generates
C. private SSH key that Cisco ScanCenter generates
D. private SSH key that the Cisco WSA generates
Correct Answer: A
Question 14:
A user browses to a company website that is categorized as “Business and Industry” and contains a Facebook post. The user cannot see the Facebook post because the category “Social Networking” is blocked. Which configuration allows the user to see the Facebook post?
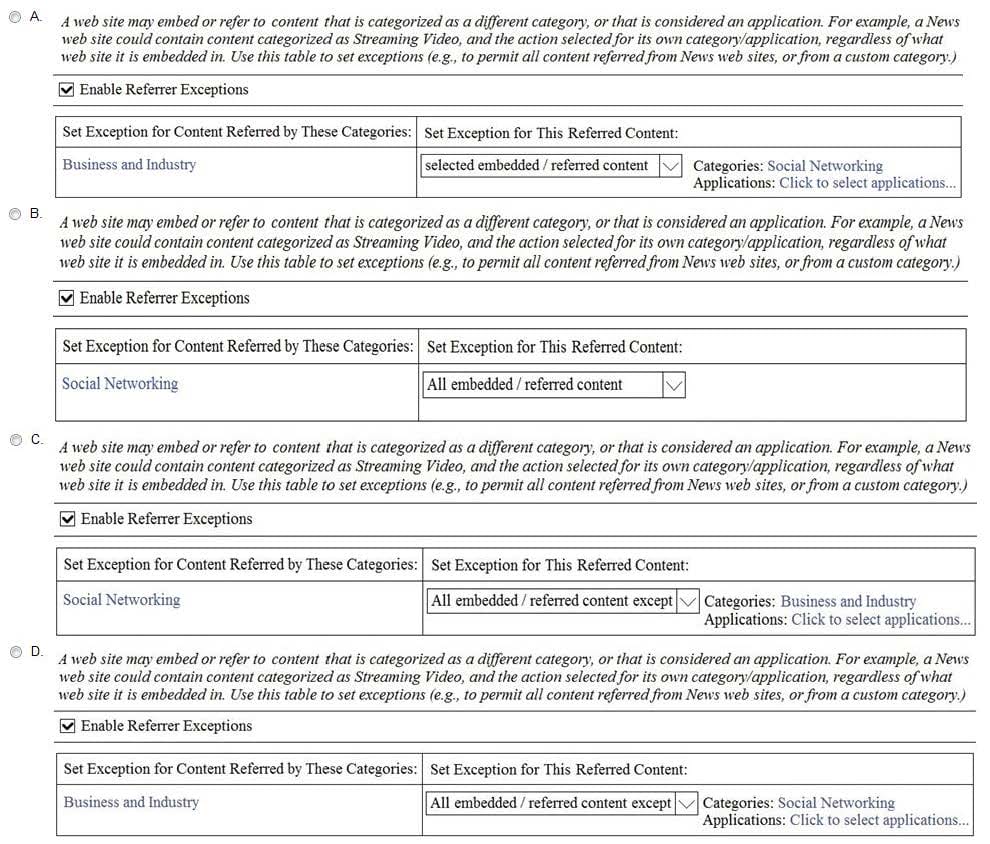
A. Option A
B. Option B
C. Option C
D. Option D
Correct Answer: A
Question 15:
Which two features can be used with an upstream and downstream Cisco WSA web proxy to have the upstream WSA identify users by their client IP address? (Choose two.)
A. X-Forwarded-For
B. high availability
C. web cache
D. via
E. IP spoofing
Correct Answer: AD
…
Summarize:
Leads4Pass 300-725 dumps provide candidates with additional validation and free practice opportunities to help them feel confident choosing the right Cisco 300-725 SWSA exam materials.
Download Leads4Pass 300-725 dumps: https://www.leads4pass.com/300-725.html to help you successfully pass the Cisco 300-725 SWSA exam on your first attempt.




