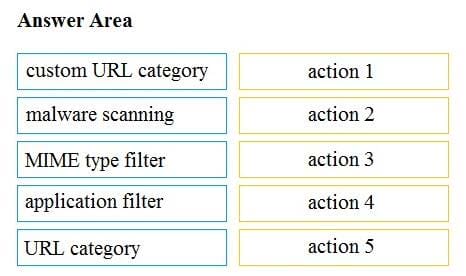
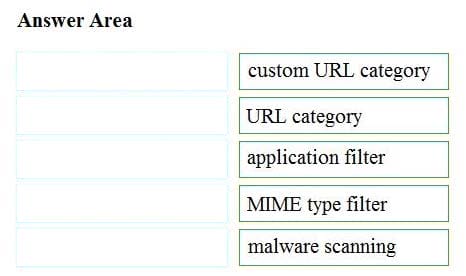
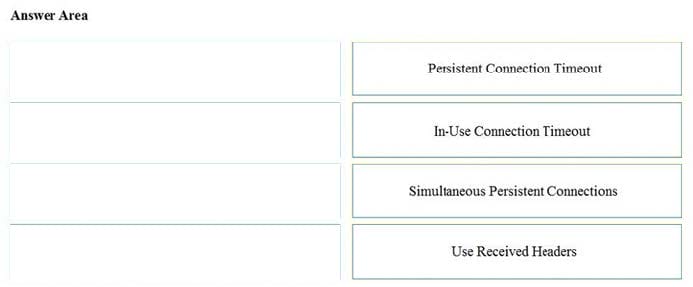
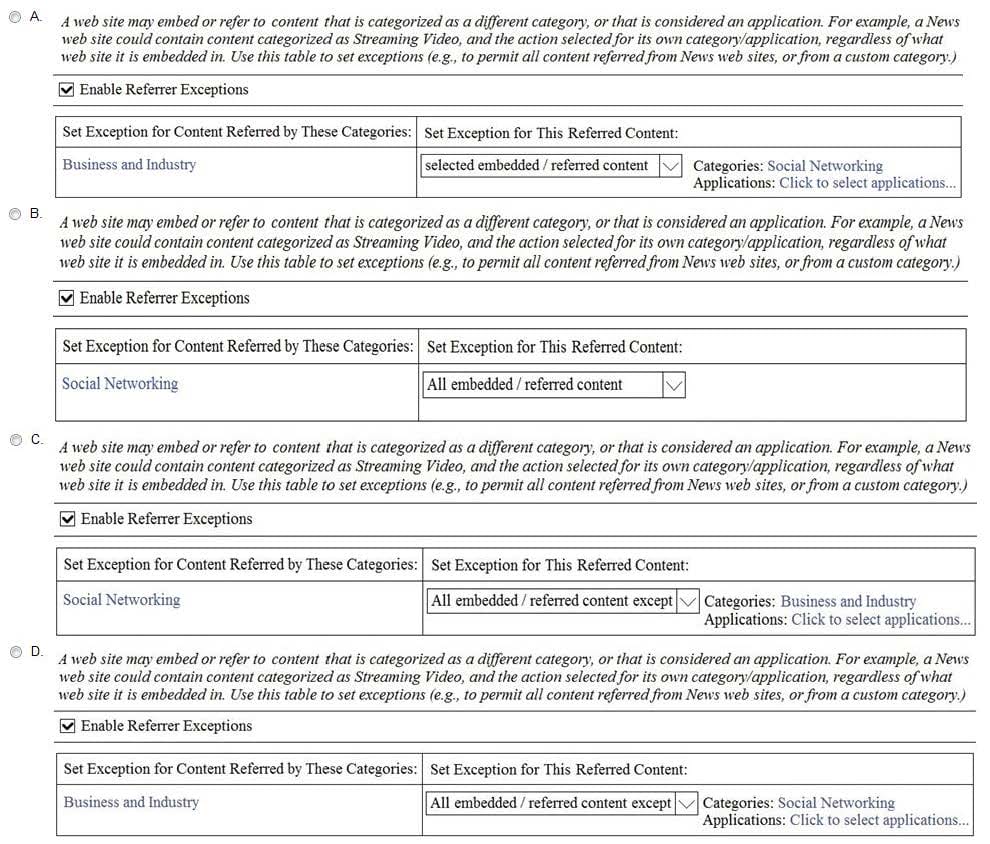
Leads4pass CCNA(V1.1) 200-301 Exam Materials updated, containing 1652 latest topic exam questions and answers, reviewed, corrected, and actually verified by the Leads4pass Cisco team to meet the CCNA certification exam requirements!
Now! Download CCNA 200-301 Exam Materials with PDF and VCE: https://www.leads4pass.com/200-301.html, practice completing CCNA 200-301 topic exam questions. 100% Guaranteed Success on Your CCNA 200-301 Exam!
Share part of the topic exam questions from Leads4pass CCNA (V1.1) 200-301 Exam Materials
| From | Number of exam questions | Associated certification | Last updated | Release time |
| Leads4pass | 15 | CCNA, CCNP Enterprise … | CCNA 200-301 dumps | Oct 2025 |
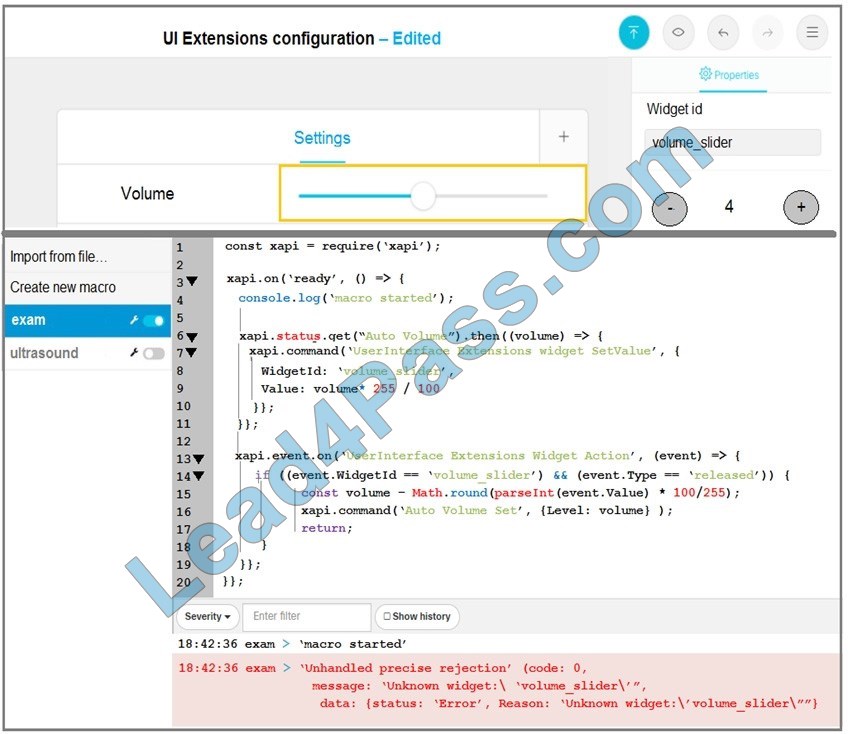
New Question 1:
Refer to the exhibit.
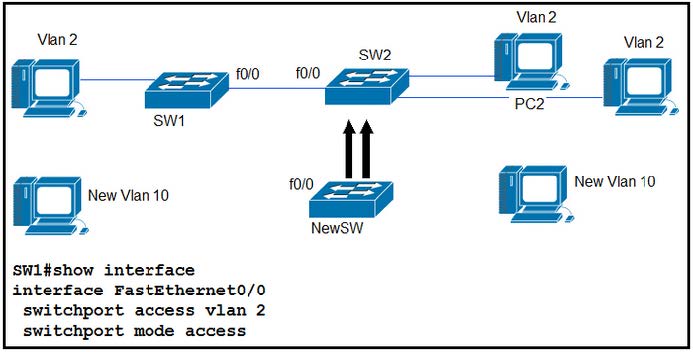
An engineer is configuring a new Cisco switch NewSW, to replace SW2 The details have been provided
1.
Switches SW1 and SW2 are third-party devices without support for trunk ports
2.
The existing connections must be maintained between PC1 PC2 and PC3
3.
Allow the switch to pass traffic from future VLAN 10.
Which configuration must be applied?
A. NewSW(config)#interface f0/0 NewSW(config-if)#switchport mode trunk NewSW(config-if)#switchport trunk native vlan 10 NewSW(config-if)#switchport trunk native vlan 10
B. NewSW(config)#interface f0/0 NewSW(config-if)#switchport mode access
NewSW(config-if)#switchport trunk allowed vlan 2, 10
NewSW(config-if)#switchport trunk native vlan 2
C. NewSW(config)#interface f0/0 NewSW(config-if)#switchport mode access NewSW(config-if)#switchport trunk allowed vlan 2, 10 NewSW(config-if)#switchport trunk native vlan 10
D. NewSW(config)#interface f0/0 NewSW(config-if)#switchport mode trunk NewSW(config-if)#switchport trunk allowed vlan 2, 10 NewSW(config-if)#switchport trunk native vlan 2
Correct Answer: D
Nothing says that the new switch doesn\’t allow trunking. It can´t be B, because when you configure the port in access mode it doesn´t evaluate the trunking commands, and access only permits one vlan.
If you have access on one side the vlan comes untagged, for the other side to put this untagged vlan in a native vlan the port needs to be configured as trunk. Also this imposes that in the future to have vlan 10 passing here you would need to replace SW1 to have trunk funcionality or alternatively configure another uplink to pass vlan 10 the same way to new SW.
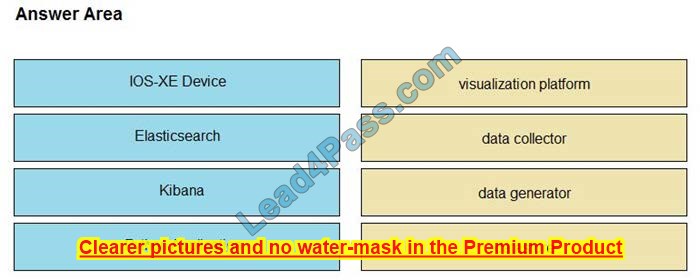
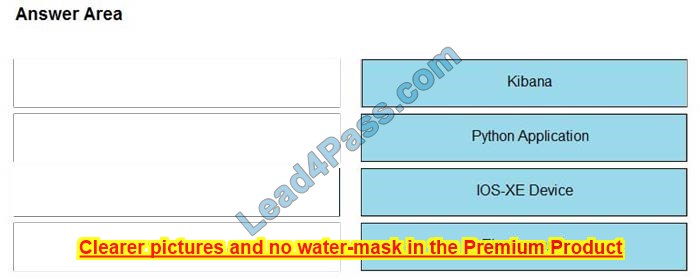
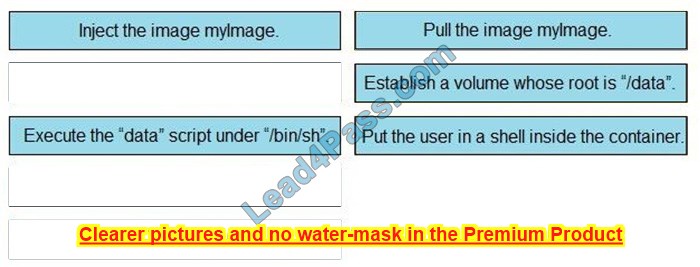
New Question 2:
DRAG DROP
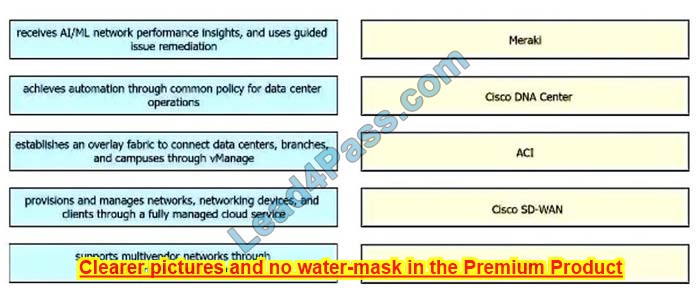
Drag the descriptions of device management from the left onto the types of device management on the right.
Select and Place:
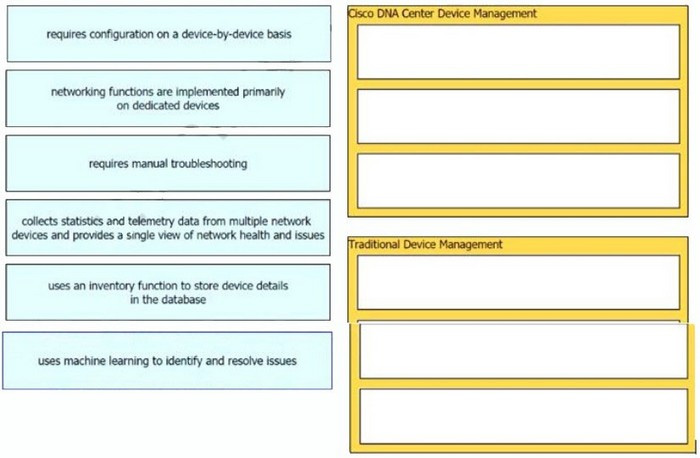
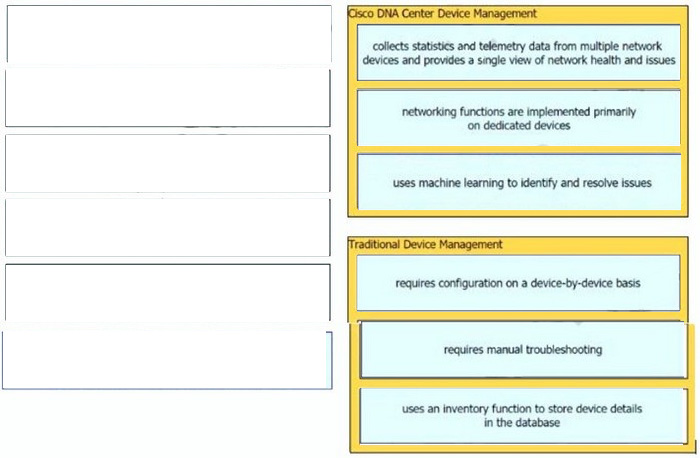
Correct Answer:
New Question 3:
Refer to the exhibit. Routers R1 and R3 have the default configuration The router R2 priority is set to 99 Which commands on R3 configure it as the DR in the 10.0 4.0/24 network?
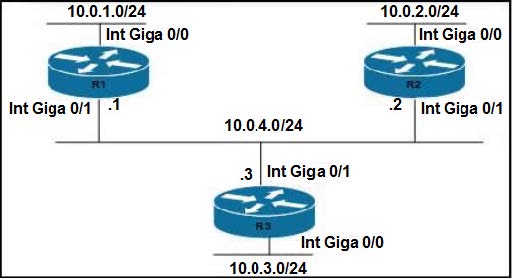
A. R3(config)#interface Gig0/1 R3(config-if)#ip ospf priority 100
B. R3(config)#interface Gig0/0 R3(config-if)#ip ospf priority 100
C. R3(config)#interface Gig0/0 R3(config-if)i=ip ospf priority 1
D. R3(config)#interface Gig0/1 R3(config-if)#ip ospf priority 0
Correct Answer: B
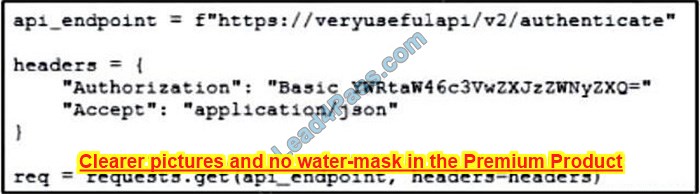
New Question 4:
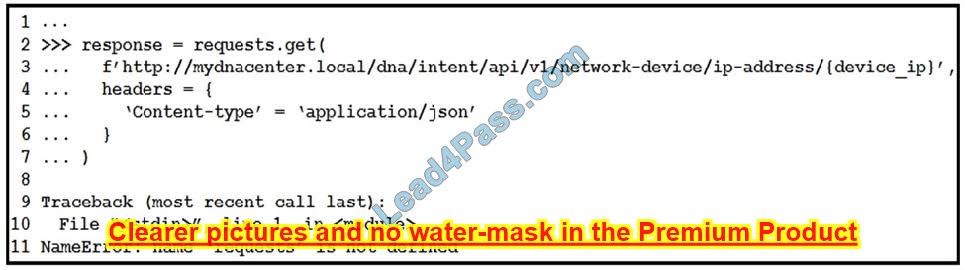
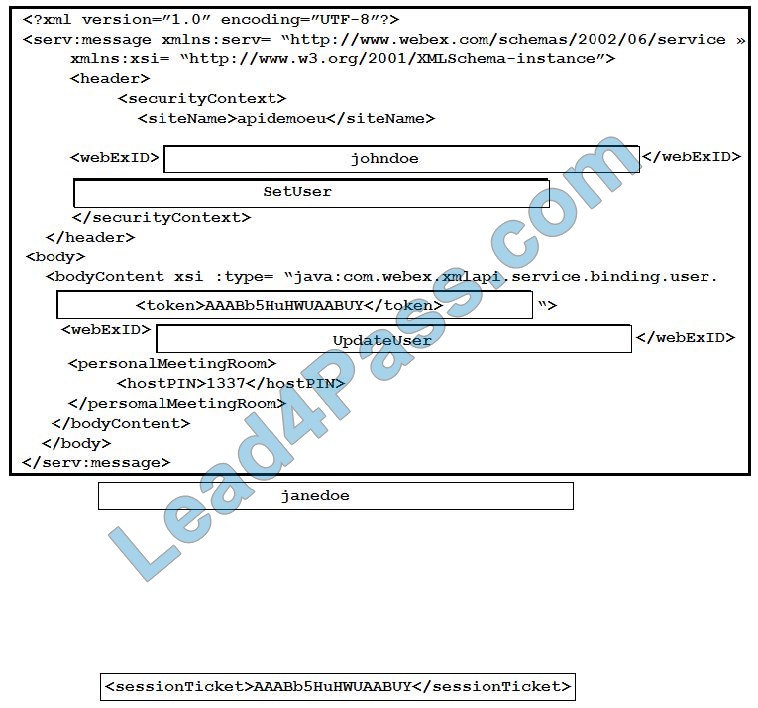
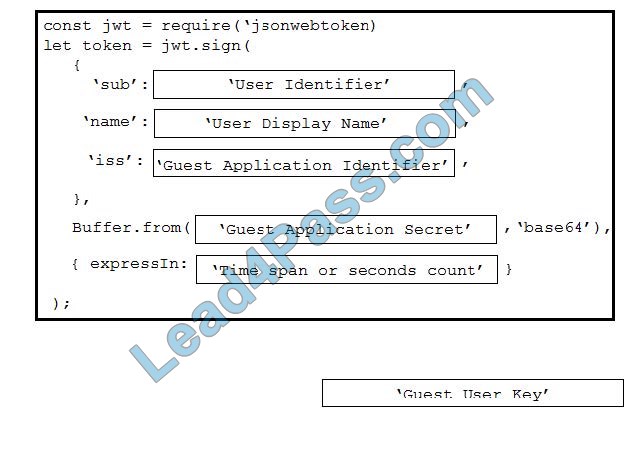
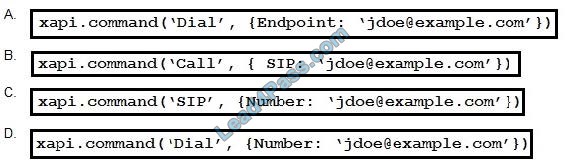
What is represented by the word “ge3/36” within this JSON schema?
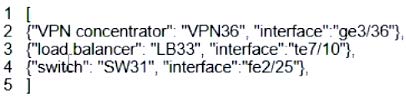
A. value
B. array
C. object
D. key
Correct Answer: A
New Question 5:
Which IPv6 address is the equivalent of the IPv4 interface loopback address 127.0.0.1?
A. ::1
B. ::
C. 2000::/3
D. 0::/10
Correct Answer: A
In IPv6 the loopback address is written as, ::1
This is a 128bit number, with the first 127 bits being \’0\’ and the 128th bit being \’1\’. It\’s just a single address, so could also be written as ::1/128.
New Question 6:
DRAG DROP
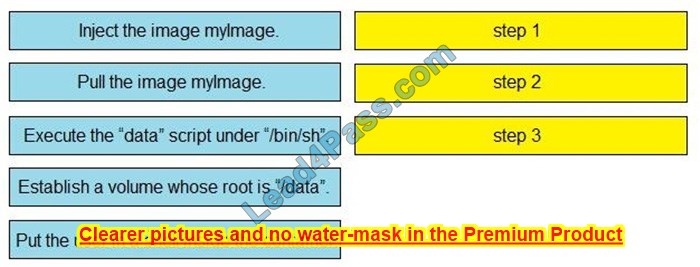
Drag and drop the characteristics of northbound APIs from the left onto any position on the right. Not all characteristics are used.
Select and Place:
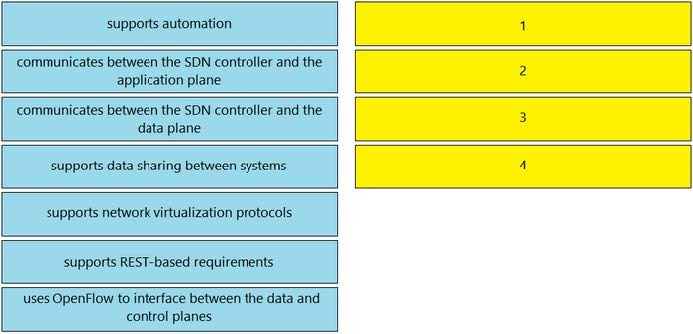
Correct Answer:
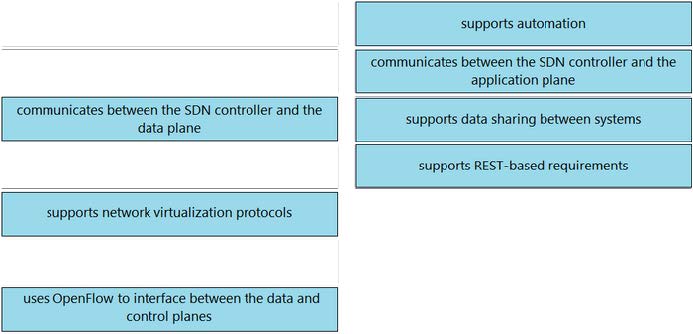
New Question 7:
Company has decided to require multifactor authentication for all systems. Which set of parameters meets the requirement?
A. personal 10-digit PIN and RSA certificate
B. complex password and personal 10-digit PIN
C. password of 8 to 15 characters and personal 12-digit PIN
D. fingerprint scanning and facial recognition
Correct Answer: A
New Question 8:
Refer to the exhibit. How will the router handle a packet destined for 192.0.2.156?
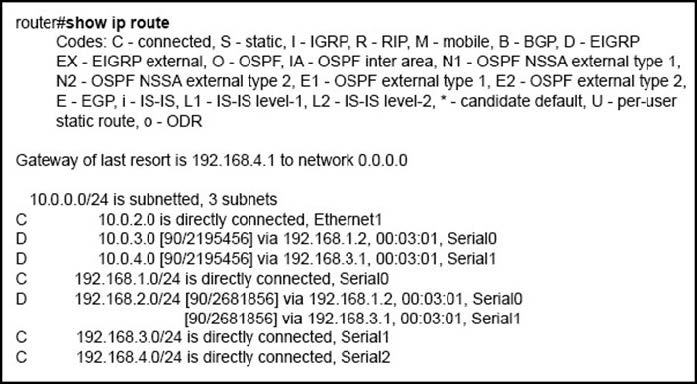
A. The router will forward the packet via either Serial0 or Serial1.
B. The router will return the packet to its source.
C. The router will forward the packet via Serial2.
D. The router will drop the packet.
Correct Answer: C
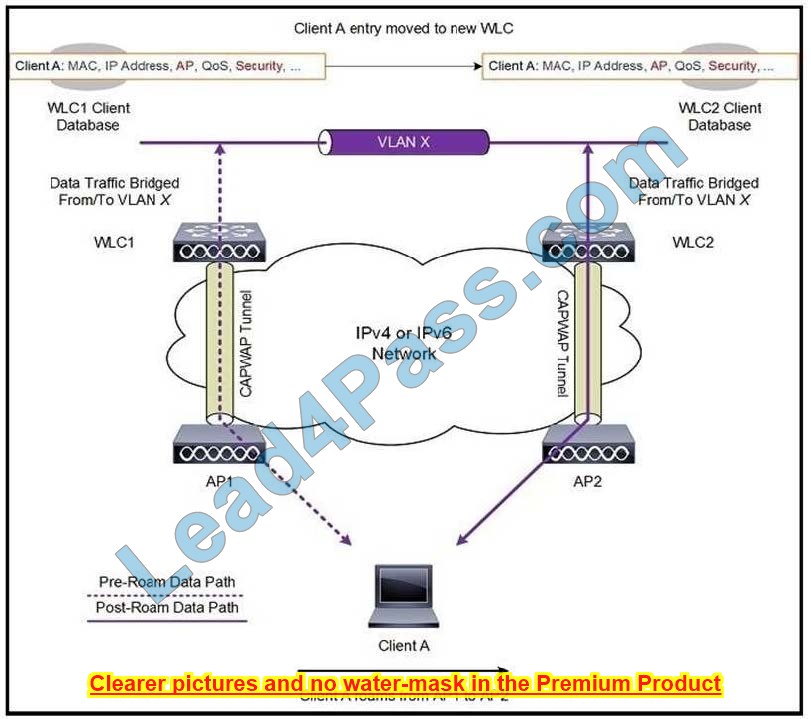
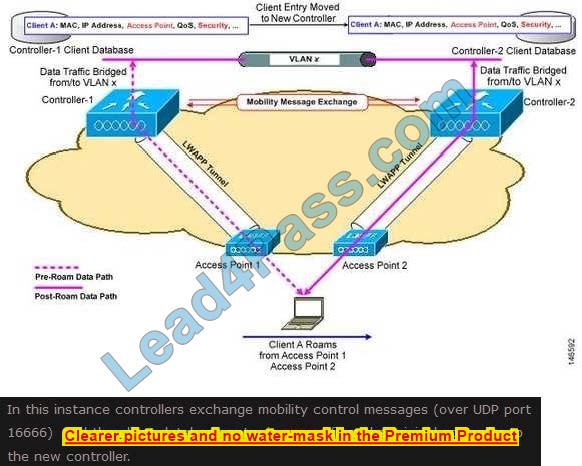
New Question 9:
An administrator must secure the WLC from receiving spoofed association requests. Which steps must be taken to configure the WLC to restrict the requests and force the user to wait 10 ms to retry an association request?
A. Enable Security Association Teardown Protection and set the SA Query timeout to 10
B. Enable MAC filtering and set the SA Query timeout to 10
C. Enable 802.1x Layer 2 security and set me Comeback timer to 10
D. Enable the Protected Management Frame service and set the Comeback timer to 10
Correct Answer: D
“You then need to specify the comeback timer and SA query timeout. The comeback timer specifies the time that an associated client must wait before the association can be tried again…” https://www.cisco.com/c/en/us/support/docs/wireless-mobility/wireless-lan-wlan/212576-configure-802-11w-management-frame-prote.html
New Question 10:
How does HSRP provide first hop redundancy?
A. It load-balances Layer 2 traffic along the path by flooding traffic out all interfaces configured with the same VLAN.
B. It uses a shared virtual MAC and a virtual IP address to a group of routers that serve as the default gateway for hosts on a LAN.
C. It forwards multiple packets to the same destination over different routed links in the data path.
D. It load-balances traffic by assigning the same metric value to more than one route to the same destination in the IP routing table.
Correct Answer: B
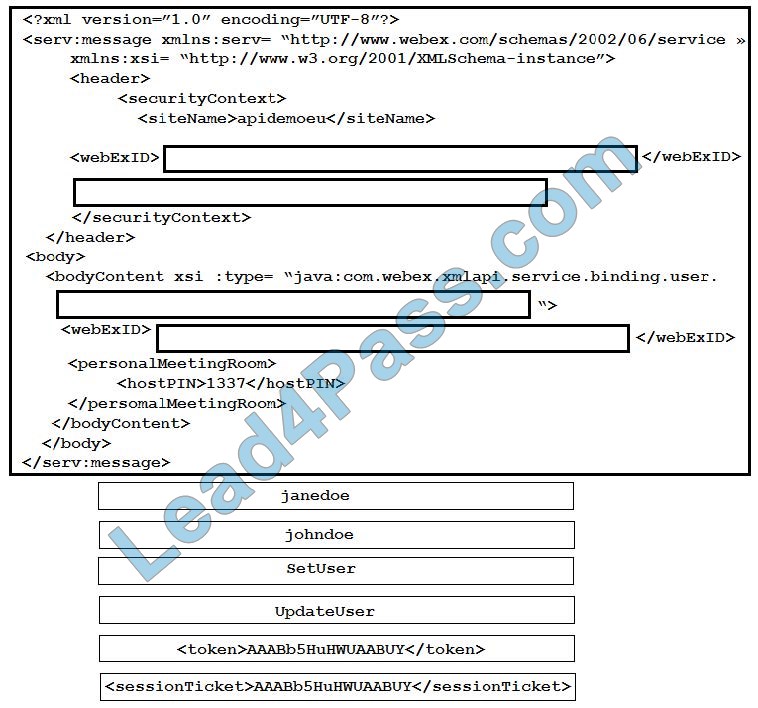
New Question 11:
DRAG DROP
Drag and drop the statements about AAA services from the left to the corresponding AAA services on the right. Not all options are used.
Select and Place:
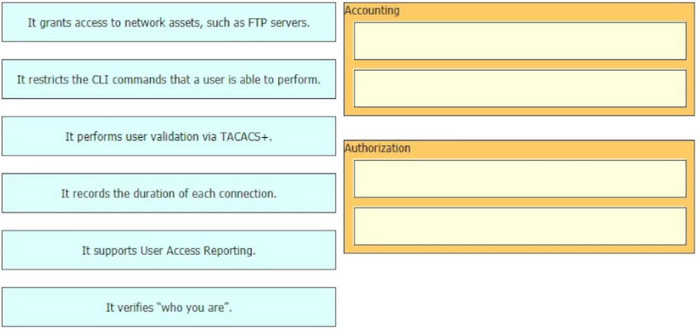
Correct Answer:
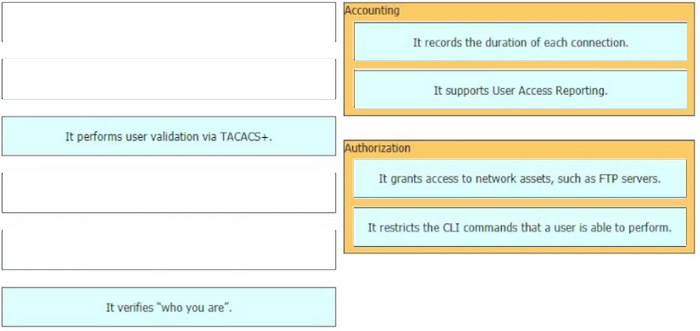
New Question 12:
Refer to the exhibit.
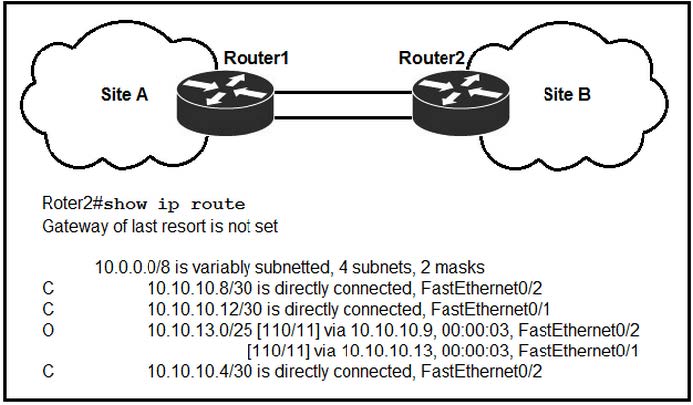
If OSPF Is running on this network, how does Router2 handle traffic from Site B to 10.10.13.128/25 at Site A?
A. It load-balances traffic out of Fa0/1 and Fa0/2.
B. It is unreachable and discards the traffic.
C. It sends packets out of interface FaO/2.
D. It sends packets out of interface Fa0/1.
Correct Answer: B
New Question 13:
Refer to the exhibit.
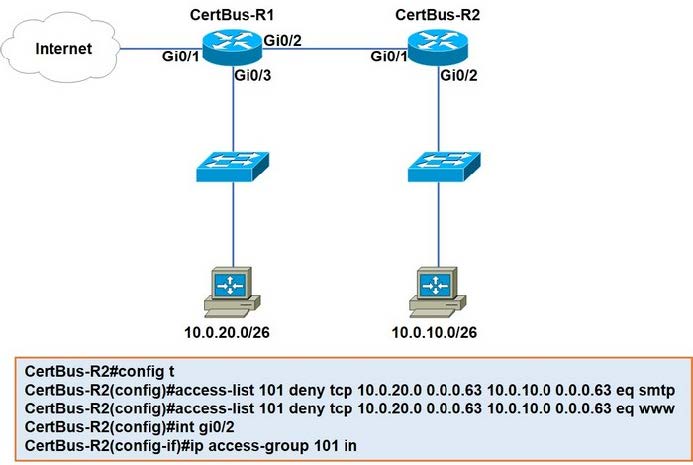
An extended ACL has been configured and applied to router R2. The configuration failed to work as intended.
Which two changes stop outbound traffic on TCP ports 25 and 80 to 10.0.20.0/26 from the 10.0.10.0/26 subnet while still allowing all other traffic? (Choose two.)
A. Add a “permit ip any any” statement at the end of ACL 101 for allowed traffic.
B. Add a “permit ip any any” statement to the beginning of ACL 101 for allowed traffic.
C. The ACL must be moved to the Gi0/1 interface outbound on R2.
D. The source and destination IPs must be swapped in ACL 101.
E. The ACL must be configured the Gi0/2 interface inbound on R1.
Correct Answer: AD
All ACLs have a implicit deny at the end which blocks all traffic so we need to add a permit to allow that traffic through
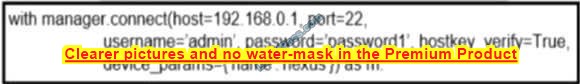
New Question 14:
Refer to the exhibit. Which configuration issue is preventing the OSPF neighbor from being established between the two routers?

A. R1 has an incorrect network command for interface Gi1/0.
B. R2 should have its network command in area 1.
C. R1 interface Gi1/0 has a larger MTU size.
D. R2 is using the passive-interface default command.
Correct Answer: C
Question 15:
Refer lo the exhibit.
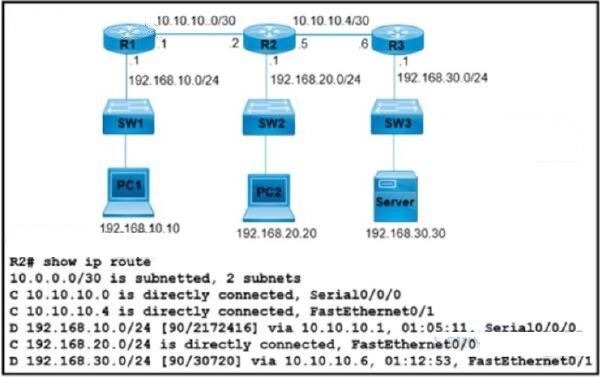
What is the next-hop P address for R2 so that PC2 reaches the application server via ElGRP?
A. 192.168.30.1
B. 10.10 105
C. 10.10.10.6
D. 192.168.201
Correct Answer: D
…
Leads4pass CCNA (V1.1) 200-301 Exam Materials cover the complete CCNA certification topic exam questions! You can experience some of the latest CCNA 200-301 Exam Materials topic exam questions through the online practice,
Help you experience the real scene in advance!
More importantly! Download CCNA 200-301 Exam Materials with PDF and VCE: https://www.leads4pass.com/200-301.html, practice completing CCNA 200-301 topic exam questions. Helping you pass the CCNA 200-301 exam with ease!