
Cisco 300-915 DEVIOT dumps have been updated! After being verified by many experienced cisco exam experts, it is 100% actually effective. leads4pass 300-915 complete exam questions and answers include two modes: PDF dumps and VCE dumps Here you can view https://www.leads4pass.com/300-915.html (Total Questions: 59 Q&A). This site shares a part of Cisco 300-915 DEVIOT free dumps, you can learn and participate in the test for free!
Cisco 300-915 DEVIOT free dumps online learning, you can participate in online testing
The answer is obtained at the end of the article
QUESTION 1
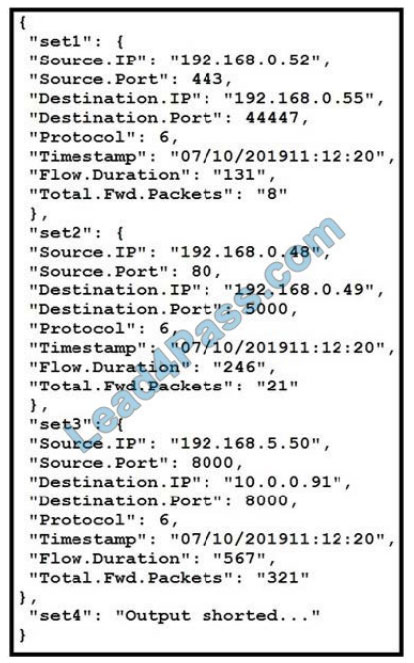
Refer to the exhibit. The code snippet provides information about the packet captures within a network.
How can the most used source IP addresses within a specific time be visualized?
A. line graph
B. bar histogram
C. scatter plot
D. heatmap
QUESTION 2
Which connector is southbound?
A. horizontal connector
B. cloud connector
C. device connector
D. universal connector
QUESTION 3
How does the Cisco router (IR) and switch (IE) portfolio support edge data services?
A. Edge data services can be run and managed as containers using Cisco IOx.
B. Edge data services can run only in virtual machines on a separate compute layer.
C. Edge data services are aliases for IR/IE configuration services.
D. Edge data services run as separate instances only on virtual machines.
QUESTION 4
A customer is deploying sensors with Cisco IR829 routers in moving trucks to continuously monitor the health of
engines using a cloud application.
Which data extraction and processing strategy is best suited in this environment?
A. No need to store data locally, upload in real time to the cloud for processing.
B. Generate local alerts and create reports at the edge, and upload to the cloud at the end of the day.
C. Use the store and forward mechanism to upload the information at the earliest to cloud.
D. Ensure that data is stored for a longer duration locally and upload to the cloud every week.
QUESTION 5
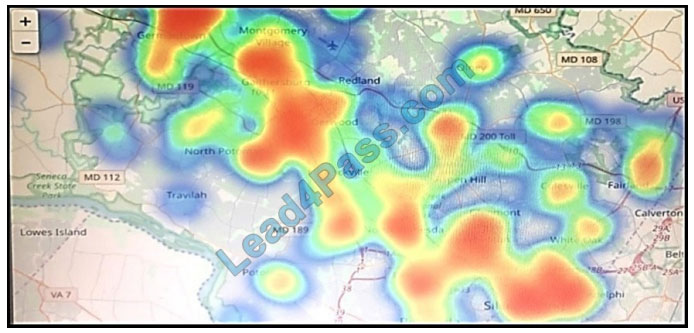
Refer to the exhibit. Which two statements are true? (Choose two.)
A. That is a heatmap projected on top of a geographic map.
B. That is a treemap projected on top of a geographic map.
C. The color red usually stands for lower values and the color blue usually stands for higher values.
D. Another suitable visualization technique for this image would be line graphs.
E. The color blue usually stands for lower values and the color red usually stands for higher values.
QUESTION 6
What are two functionalities of edge data services? (Choose two.)
A. creating a machine learning data model
B. supporting many interfaces and APIs
C. applying advanced data analytics
D. filtering, normalizing and aggregating data
E. saving data for a prolonged time period
QUESTION 7
A company is collecting data from several thousand machines globally. Which software component in the overall
architecture is the next destination of the dataflow after the data has been gathered and normalized on the edge data
software?
A. relational database: MySQL
B. historian database: influxDB
C. message broker: Apache Kafka
D. dashboard: Node.js web app
QUESTION 8

Refer to the exhibit. Approximately 4000 oil platforms, each with 400 sensors, are spread in the Gulf of Mexico and all of their data must come together into one dashboard. Which general architecture should be selected to connect them?
A. 4-tier: sensor ?edge device (Intel Atom CPU) ?fog device (Intel Xeon CPU) ?cloud
B. 5-tier: intelligent sensor?edge device (Intel Atom CPU) ?fog device (Intel Xeon CPU) ?edge data center (Intel Xeon
CPU)
C. 2-tier: intelligent sensor ?cloud
D. 3-tier: sensor ?edge device (Intel Atom CPU) ?cloud
QUESTION 9
Which element ensures that PKI is used to establish the identity of IoT devices?
A. unique device identifier
B. encryption key
C. air gap
D. hashed routes
QUESTION 10
After an application is deployed, potential issues arise around connectivity. As part of the troubleshooting process, the
IP address must be determined to ensure end-to-end communication.
Which method provides the required details using the Cisco IOx CLI?
A. ioxclient application status
B. ioxclient application metrics
C. ioxclient application getconfig
D. ioxclient application info
QUESTION 11
As part of an IoT project, an organization is developing an application that will share multiple clients using a REST API.
Based on the software development process, what are two valid technical activities that can be suggested to secure the
REST API that is developed during the development of the software? (Choose two.)
A. Respond to request failures in detail to allow users for easier troubleshooting.
B. Implement HTTP whitelisting to only methods that are allowed.
C. Implement and review audit logs for security-related events.
D. Reject HTTP methods that are invalid with an error code 404.
E. Implement physical firewalling and access control to the resources.
QUESTION 12
When constructing a Python script for data extraction using GMM APIs on a Cisco Kinetic Cloud platform, how should
the API authentication be implemented?
A. Generate the API keys once and edit the permissions as needed.
B. Generate and use the API keys for the required access level from the Kinetic Cloud application.
C. Use a complex username and password with 128-bit encryption.
D. Use a complex username with an auto-generated password from the Kinetic Cloud application.
QUESTION 13

Refer to the exhibit. The code and the error message that are received when the code is run is presented.
What causes issues authenticating with Cisco GMM API using the web-generated API key?
A. firewall that blocks authentication ports
B. incorrect username and password
C. incorrect GMM Cluster selection
D. incorrect key size and data encryption
QUESTION 14
DRAG DROP
Drag and drop the Dockerfile instructions from the left onto the correct arguments on the right.
Select and Place:
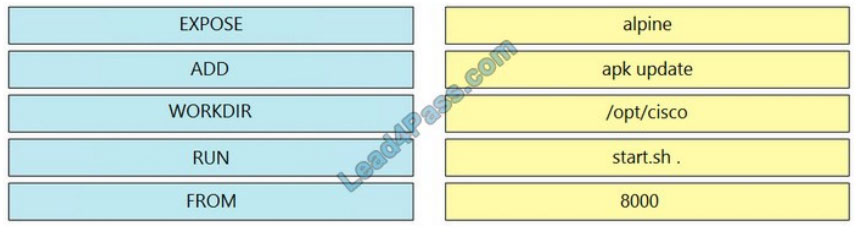
Correct Answer:
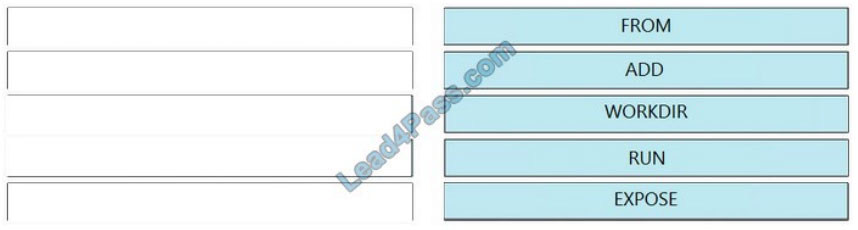
QUESTION 15
As part of an IoT project, an organization is developing an edge application that will run on a gateway to securely
transmit sensor information it receives into an IoT cloud. Based on the Agile software development lifecycle, the
development team is planning to implement a CI/CD pipeline.
Which two methods should be suggested to make the software development lifecycle more secure during the
implementation and testing? (Choose two.)
A. Perform automated code reviews prior to deployment.
B. Implement auto-provisioning security inspection for the code.
C. Perform on-going penetration testing on the system.
D. Perform a GAP analysis on current security activities and policies.
E. Train members of the team in a secure software development lifecycle methodology such as OWASP.
Verify answer:
| Q1 | Q2 | Q3 | Q4 | Q5 | Q6 | Q7 | Q8 | Q9 | Q10 | Q11 | Q12 | Q13 | Q14 | Q15 |
| B | C | C | B | AE | DE | B | B | A | D | BD | B | B | IMAGE | DE |
Free Cisco 300-915 DEVIOT exam PDF download online
Google Drive: https://drive.google.com/file/d/1fXdnq4xilUOcY7pT3qymmiqBkvOS1Bos/
The above shared the latest Cisco 300-915 DEVIOT free dumps and exam PDF. All exam questions are from leads4pass 300-915 dumps. Here https://www.leads4pass.com/300-915.html. Get the complete Exam dump!
Help you pass the exam successfully. Like, please bookmark and share!
PS. VceCert collects free exam dumps of all Cisco series. You can find all Cisco exam questions and answers!




