Share real and effective Microsoft IT Infrastructure 98-367 exam dumps for free. 13 Online 98-367 Exam Practice test questions and answers, online 98-367 pdf download, easy to learn! Get the full 98-367 Dumps: https://www.leads4pass.com/98-367.html (Total Questions: 244 Q&A) to make it easy to pass the exam!
[PDF] Free Microsoft IT Infrastructure 98-367 pdf dumps download from Google Drive: https://drive.google.com/open?id=14gwb7N7QVBYbfV2F1l-bH3gDl3On2hpT
[PDF] Free Full Microsoft pdf dumps download from Google Drive: https://drive.google.com/open?id=1AwBFPqkvdpJBfxdZ3nGjtkHQZYdBsRVz
Exam 98-367: Security fundamentals – Microsoft: https://www.microsoft.com/en-us/learning/exam-98-367.aspx
Skills measured
- Understand security layers (25–30%)
- Understand operating system security (35-40%)
- Understand network security (20–25%)
- Understand security software (15–20%)
Microsoft Certification Exam List | Microsoft Learning: https://www.microsoft.com/en-us/learning/exam-list.aspx
Pass the Microsoft Exam checklist: https://www.leads4pass.com/microsoft.html
Latest effective Microsoft IT Infrastructure 98-367 Exam Practice Tests
QUESTION 1
Where should you lock up the backup tapes for your servers?
A. The server room
B. A filing cabinet
C. The tape library
D. An offsite fire safe
Correct Answer: D
Explanation
Backup tapes should be stored off site, preferably in a fire safe, so that the data is available should a fire, flood, or other
disaster affect the location were the servers are.
QUESTION 2
Password history policies are used to prevent:
A. Brute force attacks
B. Users from sharing passwords
C. Social engineering
D. Passwords from being reused immediately
Correct Answer: D
Explanation
This security setting determines the number of unique new passwords that have to be associated with a user account
before an old password can be reused. The value must be between 0 and 24 passwords. This policy enables
administrators to enhance security by ensuring that old passwords are not reused continually. Reference:
http://technet.microsoft.com/en-us/library/cc758950(v=ws.10).aspx
QUESTION 3
Role separation improves server security by:
A. Enforcing principle of least privilege.
B. Installing applications on separate hard disks.
C. Physically separating high security servers from other servers.
D. Placing servers on separate VLANs.
Correct Answer: A
Explanation
QUESTION 4
When conducting a security audit the first step is to:
A. Inventory the company\\’s technology assets
B. Install auditing software on your servers
C. Set up the system logs to audit security events
D. Set up a virus quarantine area
Correct Answer: A
Explanation
QUESTION 5
Setting a minimum password age restricts when users can:
A. Request a password reset
B. Change their passwords
C. Log on by using their passwords
D. Set their own password expiration
Correct Answer: B
Explanation
Configure the minimum password age to be more than 0 if you want Enforce password history to be effective. Without a
minimum password age, users can cycle through passwords repeatedly until they get to an old favorite.
QUESTION 6
Basic security questions used to reset a password are susceptible to:
A. Hashing
B. Social engineering
C. Network sniffing
D. Trojan horses
Correct Answer: B
Explanation
Reference: http://en.wikipedia.org/wiki/Self-service_password_reset
QUESTION 7
The certificate of a secure public Web server on the Internet should be: A. Issued by a public certificate authority (CA)
B. Signed by using a 4096-bit key
C. Signed by using a 1024-bit key
D. Issued by an enterprise certificate authority (CA)
Correct Answer: A
Explanation
QUESTION 8
For each of the following statements, select Yes if the statement is true. Otherwise, select No. Each correct selection is
worth one point.
Hot Area: Hot Area:
Hot Area:  Correct Answer:
Correct Answer: 
QUESTION 9
The Windows Firewall protects computers from unauthorized network connections.
Select the correct answer if the underlined text does not make the statement correct. Select “No change is needed\\’\\’ if
the underlined text makes the statement correct.
A. Email viruses
B. Phishing scams
C. Unencrypted network access
D. No change is needed
Correct Answer: D
Explanation
QUESTION 10
Which attack listens to network traffic of a computer resource?
A. Resource gathering
B. Denial of service
C. ARP poisoning
D. Eavesdropping
E. Logic bomb
Correct Answer: D
Explanation
Eavesdropping In general, the majority of network communications occur in an unsecured or “cleartext” format, which
allows an attacker who has gained access to data paths in your network to “listen in” or interpret (read) the traffic. When
an attacker is eavesdropping on your communications, it is referred to as sniffing or snooping. The ability of an
eavesdropper to monitor the network is generally the biggest security problem that administrators face in an enterprise.
Without strong encryption services that are based on cryptography, your data can be read by others as it traverses the
network.
QUESTION 11
Cookies impact security by enabling: (Choose two.)
A. Storage of Web site passwords.
B. Higher security Web site protections.
C. Secure Sockets Layer (SSL).
D. Web sites to track browsing habits.
Correct Answer: AD
Explanation
Reference: http://en.wikipedia.org/wiki/HTTP_cookie
QUESTION 12
You have two servers that run Windows Server. All drives on both servers are formatted by using NTFS. You move a
file from one server to the other server. The file\\’s permissions in the new location will:
A. Enable full access to the everyone group
B. Restrict access to the Administrators group
C. Inherit the destination folder\\’s permissions
D. Retain the original folder\\’s permissions
Correct Answer: C
Explanation
You can modify how Windows Explorer handles permissions when objects are copied or moved to another NTFS
volume. When you copy or move an object to another volume, the object inherits the permissions of its new folder.
QUESTION 13
You suspect a user\\’s computer is infected by a virus. What should you do first?
A. Restart the computer in safe mode
B. Replace the computer\\’s hard disk drive
C. Disconnect the computer from the network
D. Install antivirus software on the computer
Correct Answer: D
Explanation
Share 13 of the latest Microsoft IT Infrastructure 98-367 exam questions and answers for free to help you improve your skills and experience! Easily select the complete 98-367 Dumps: https://www.leads4pass.com/98-367.html (Total Questions: 244 Q&A) through the exam! Guaranteed to be true and effective! Easily pass the exam!
Who should take this exam?
This exam validates that a candidate has fundamental security knowledge and skills. It can serve as a stepping stone to the Microsoft Certified Solutions Associate (MCSA) exams. It is recommended that candidates become familiar with the concepts and the technologies described here by taking relevant training courses. Candidates are expected to have some hands-on experience with Windows Server, Windows-based networking, Active Directory, anti-malware products, firewalls, network topologies and devices, and network ports.
[PDF] Free Microsoft IT Infrastructure 98-367 pdf dumps download from Google Drive: https://drive.google.com/open?id=14gwb7N7QVBYbfV2F1l-bH3gDl3On2hpT
[PDF] Free Full Microsoft pdf dumps download from Google Drive: https://drive.google.com/open?id=1AwBFPqkvdpJBfxdZ3nGjtkHQZYdBsRVz
leads4pass Promo Code 12% Off
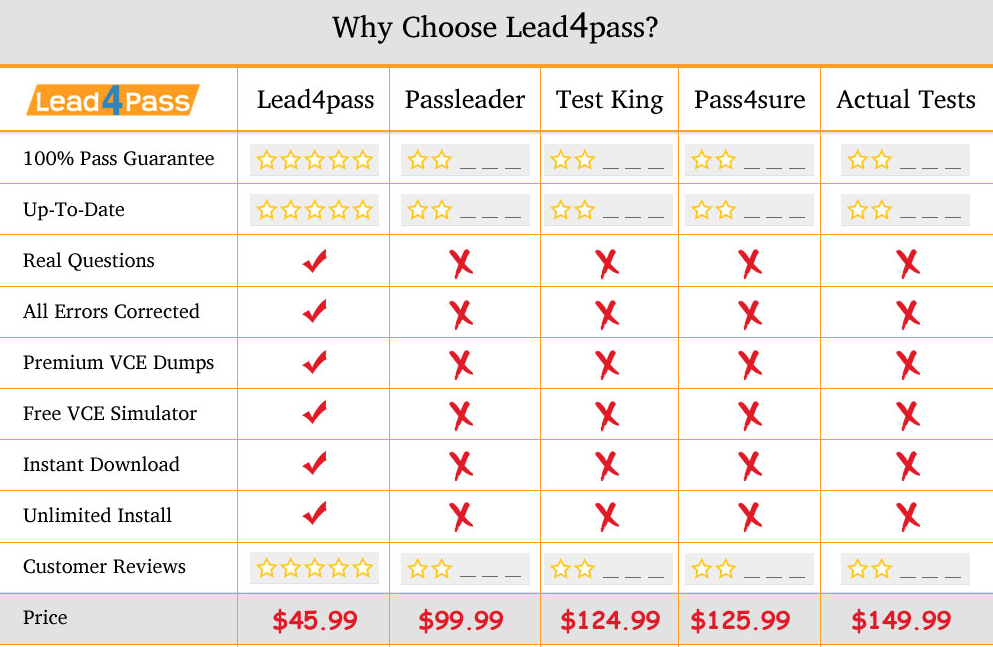
Why Choose leads4pass?
Candidates for this exam have fundamental knowledge of Windows devices and mobility. Candidates should have some hands-on experience with Windows devices, Windows-based networking, Active Directory, antimalware products, firewalls, network topologies and devices, and network ports.
related more: Latest CompTIA A+ 220-801 Dumps Exam Practice Materials And Youtube | High Quality leads4pass Latest IT Cert Exam Dumps Free Update



