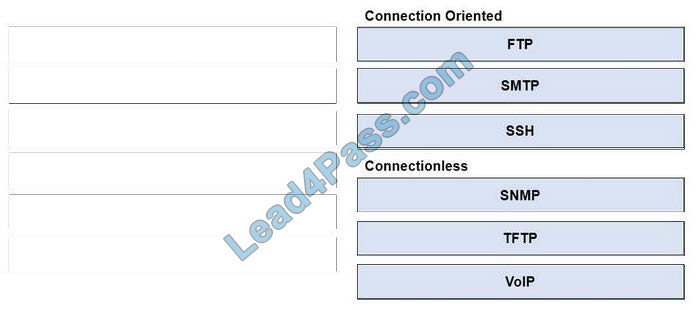
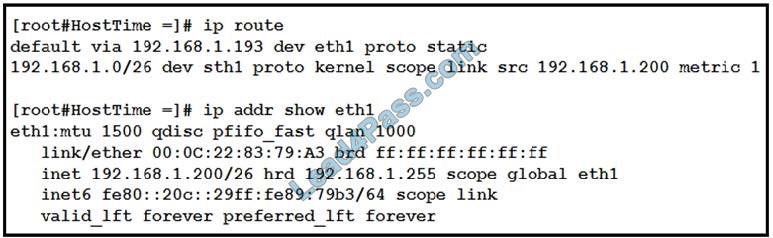
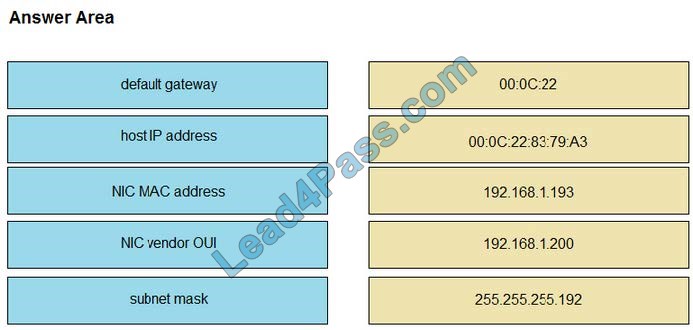
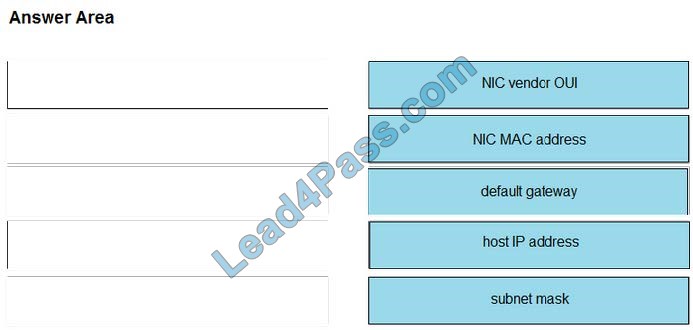
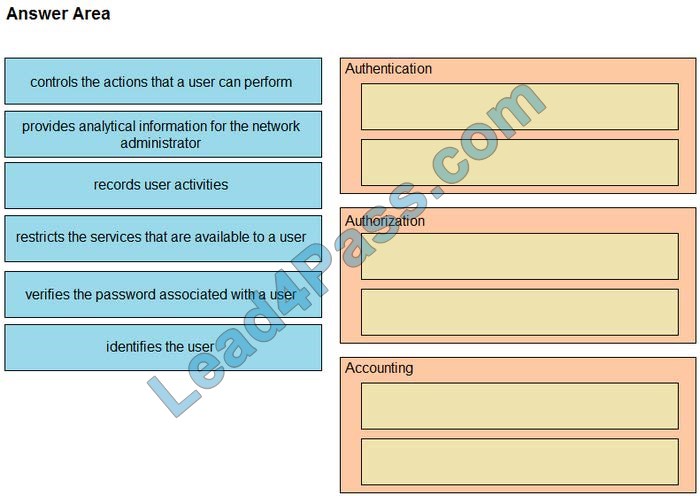
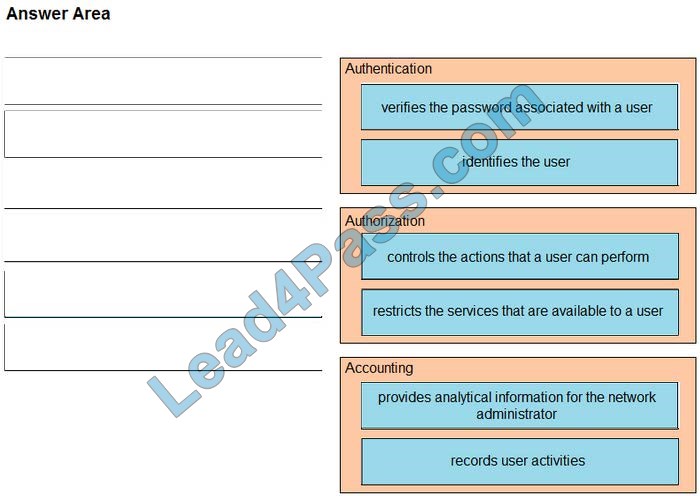
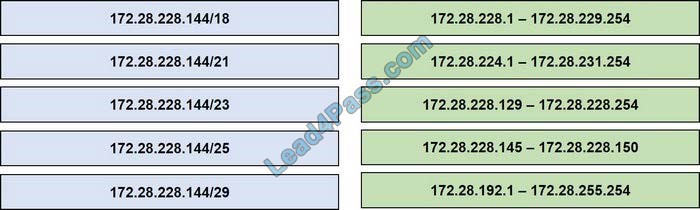
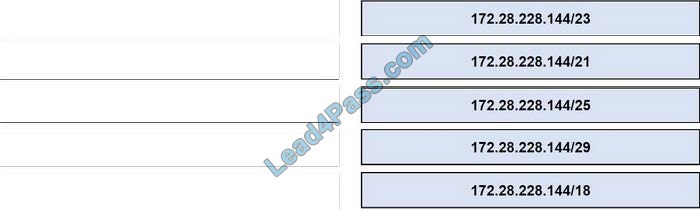
Latest CompTIA Linux+ LX0-101 dumps pdf training resources and vce youtube demo update free shared. “CompTIA Linux+ [Powered by LPI] Exam 1” is the name of CompTIA Linux+ https://www.leads4pass.com/lx0-101.html exam dumps which covers all the knowledge points of the real CompTIA exam. New CompTIA Linux+ LX0-101 dumps exam practice files download to have a free try from leads4pass.
The best and most updated useful CompTIA Linux+ LX0-101 dumps pdf training resources which are the best for clearing LX0-101 exam test, and to get certified by CompTIA Linux+. 100% success and guarantee to pass CompTIA LX0-101 exam test quickly and easily at first attempt.
High quality CompTIA LX0-101 dumps pdf training resources: https://drive.google.com/open?id=0B_7qiYkH83VRZ3FjZ01MVnQ3Rjg
High quality CompTIA LX0-102 dumps pdf training resources: https://drive.google.com/open?id=0B_7qiYkH83VRZ3hRVkZpZk5lN28
QUESTION 1
Which of the following directories contains additional information about installed packages?
A. /usr/share/documentation
B. /usr/local/share/documentation
C. /usr/local/doc
D. /usr/share/doc
E. /usr/packages/doc
Correct Answer: D
QUESTION 2
Which of the following commands will allow an administrator to adjust the number of mounts after which an existing filesystem will be checked by e2fsck?
A. debugfs
B. dumpe2fs
C. mode2fs
D. tune2fs
E. mke2fs
Correct Answer: D
QUESTION 3 CORRECT TEXT
In which directory must definition files be placed to add additional repositories to yum?
Correct Answer: /ETC/YUM.REPOS.D,/ETC/YUM.REPOS.D/,YUM.REPOS.D,YUM.REPOS.D/
QUESTION 4
An administrator is looking for an executable file foo. Which of the following commands would search for foo within directories set in the shell variable, PATH? LX0-101 dumps
A. locate
B. which
C. find
D. query
E. whereis
Correct Answer: B
QUESTION 5
Which of the following command lines would an administrator use to restrict the GNU find command to searching a particular number of subdirectories?
A. –max-dirs
B. -dirmax
C. -maxdepth
D. -s
E. -n
Correct Answer: C
QUESTION 6
The lspci command can display information about devices EXCEPT:
A. card bus speed (e.g. 66Mhz).
B. card IRQ settings.
C. card vendor identification.
D. card AGP rate (e.g. 1x, 2x, 4x).
E. card Ethernet MAC address.
Correct Answer: E
QUESTION 7
In compliance with the FHS, in which of the following places are man pages typically found?
A. /usr/share/man
B. /opt/man
C. /usr/doc/
D. /var/pkg/man
E. /usr/local/man
Correct Answer: A
QUESTION 8 CORRECT TEXT
The system configuration file named is commonly used to set the default runlevel. (Please provide the fill name with full path information).
Correct Answer: /ETC/INITTAB
QUESTION 9
In the vi editor, which of the following commands will delete the current line at the cursor and the 16 lines following it (17 lines total)? LX0-101 dumps
A. 17d
B. 17dd
C. 17x
D. d17d
E. 16d
Correct Answer: B
QUESTION 10
All of the following commands will update the Modify timestamp on the file /tmp/myfile.txt EXCEPT:
A. file /tmp/myfile.txt
B. echo “Hello” >/tmp/myfile.txt
C. sed -ie “s/1/2/” /tmp/myfile.txt
D. echo -n “Hello” >/tmp/myfile.txt
E. touch /tmp/myfile.txt
Correct Answer: A
QUESTION 11 CORRECT TEXT
What command with all options and/or parameters will send the signal USR1 to any executing process of program apache2?
Correct Answer: KILLALL-SSIGUSR1APACHE2,KILLALL-SUSR1APACHE2,KILLALLSIGUSR1APACHE2,KILLALL-USR1APACHE2
QUESTION 12
An administrator wishes to kill a process with a PID of 123. Which of the following commands will allow the process to “clean up” before exiting?
A. kill -1 123
B. kill -9 123
C. kill -15 123
D. kill -17 123
Correct Answer: C
QUESTION 13
An administrator has just added a CD-ROM drive (/dev/hdd) to a system and added it to the administrator’s fstab. Typically the administrator can use which of the following commands to mount media in that drive to /mnt/cdrom?
A. mount /dev/cdrom /mnt/cdrom
B. mount /dev/cdrom
C. mount -t cdrom /dev/cdrom /mnt/cdrom
D. mount /mnt/cdrom
E. automount /mnt/hdd /mnt/cdrom}
Correct Answer: D
QUESTION 14
To what environment variable will an administrator assign or append a value if the administrator needs to tell the dynamic linker to look in a build directory for some of a program’s shared libraries?
A. LD_LOAD_PATH
B. LD_LIB_PATH
C. LD_LIBRARY_PATH
D. LD_SHARE_PATH
E. LD_RUN_PATH
Correct Answer: C
QUESTION 15
Pressing the Ctrl-C combination on the keyboard while a command is executing in the foreground sends which of following signal codes?
A. 1 (SIGHUP)
B. 2 (SIGINT)
C. 3 (SIGQUIT)
D. 9 (SIGKILL)
E. 15 (SIGTERM)
Correct Answer: B
Useful latest CompTIA Linux+ https://www.leads4pass.com/lx0-101.html dumps pdf training materials and study guides free download from leads4pass. High quality CompTIA Linux+ LX0-101 dumps exam questions and answers free update, pass CompTIA LX0-101 exam test easily at first try.
High quality CompTIA Linux+ LX0-101 dumps vce youtube: https://youtu.be/NpGk33evqRs