CEH v11 certification exam candidates, you can now use the 312-50V11 dumps exam material to help you successfully pass the exam.
What you need to know CEH is the first in a series of 3 comprehensive courses (CEH, ECSA, and APT courses) designed to help cybersecurity masters in penetration testing.
So CEH v11 certification exam is really hard. Therefore, leads4pass strongly recommends choosing 312-50V11 dumps https://www.leads4pass.com/312-50v11.html to help you practice,
And guarantee your first attempt to successfully pass the CEH v11 certification exam.
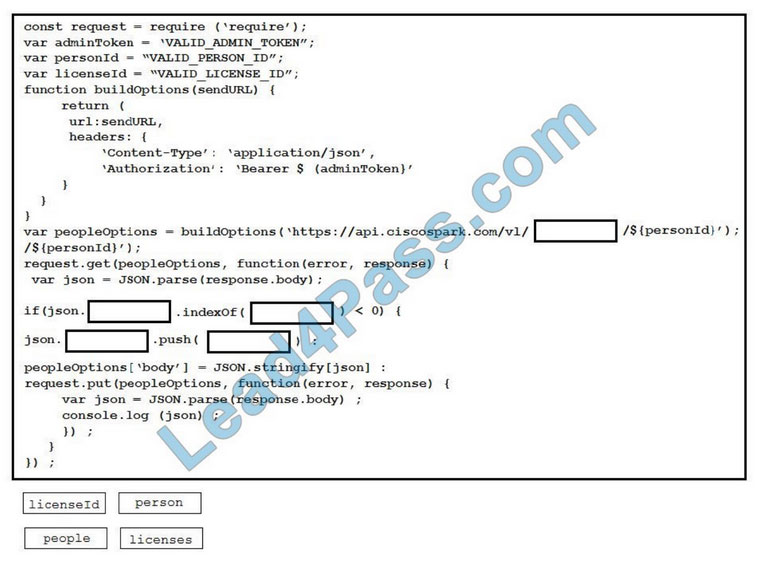
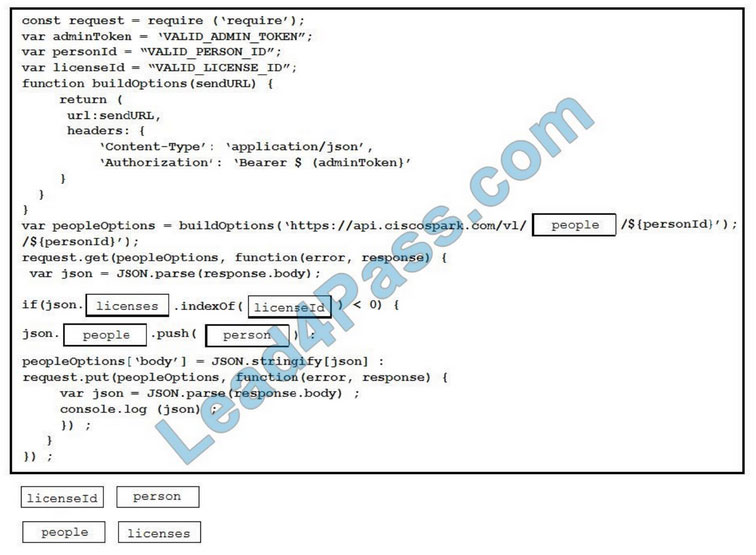
Part of the 312-50V11 dumps exam material online practice test:
Answers are announced at the end of the article
QUESTION 1:
“……..is an attack-type for a rogue Wi-Fi access point that appears to be a legitimate one offered on the premises, but actually has been set up to eavesdrop on wireless communications. It is the wireless version of the phishing scam. An attacker fools wireless users into connecting a laptop or mobile phone to a tainted hot spot by posing as a legitimate provider. This type of attack may be used to steal the passwords of unsuspecting users by either snooping the communication link or by phishing, which involves setting up a fraudulent website and luring people there.”
Fill in the blank with the appropriate choice.
A. Evil Twin Attack
B. Sinkhole Attack
C. Collision Attack
D. Signal Jamming Attack
QUESTION 2:
How can rainbow tables be defeated?
A. Use of non-dictionary words
B. All uppercase character passwords
C. Password salting
D. Lockout accounts under brute force password cracking attempts
QUESTION 3:
You want to analyze packets on your wireless network. Which program would you use?
A. Wireshark with Airpcap
B. Airsnort with Airpcap
C. Wireshark with Winpcap
D. Ethereal with Winpcap
QUESTION 4:
Nicolas just found a vulnerability on a public-facing system that is considered a zero-day vulnerability. He sent an email to the owner of the public system describing the problem and how the owner can protect themselves from that vulnerability. He also sent an email to Microsoft informing them of the problem that their systems are exposed to. What type of hacker is Nicolas?
A. Red hat
B. white hat
C. Black hat
D. Gray hat
QUESTION 5:
Ron, a security professional, was pen testing web applications and SaaS platforms used by his company. While testing, he found a vulnerability that allows hackers to gain unauthorized access to API objects and perform actions such as view, updating, and delete sensitive data of the company. What is the API vulnerability revealed in the above scenario?
A. Code injections
B. Improper use of CORS
C. No ABAC validation
D. Business logic flaws
QUESTION 6:
A regional bank hires your company to perform a security assessment on their network after a recent data breach. The attacker was able to steal financial data from the bank by compromising only a single server. Based on this information, what should be one of your key recommendations to the bank?
A. Place a front-end web server in a demilitarized zone that only handles external web traffic
B. Require all employees to change their anti-virus program with a new one
C. Move the financial data to another server on the same IP subnet
D. Issue new certificates to the web servers from the root certificate authority
QUESTION 7:
Bobby, an attacker, targeted a user and decided to hijack and intercept all their wireless communications.
He installed a fake communication tower between two authentic endpoints to mislead the victim. Bobby used this virtual tower to interrupt the data transmission between the user and the real tower, attempting to hijack an active session, upon receiving the users request. Bobby manipulated the traffic with the virtual
tower and redirected the victim to a malicious website.
What is the attack performed by Bobby in the above scenario?
A. Wardriving
B. KRACK attack
C. jamming signal attack
D. aLTEr attack
QUESTION 8:
Firewalk has just completed the second phase (the scanning phase) and a technician receives the output shown below.
What conclusions can be drawn based on these scan results?
TCP port 21 no response
TCP port 22 no response
TCP port 23 time-to-live exceeded
A. The lack of response from ports 21 and 22 indicates that those services are not running on the destination server
B. The scan on port 23 was able to make a connection to the destination host prompting the firewall to respond with a TTL error
C. The scan on port 23 passed through the filtering device. This indicates that port 23 was not blocked at the firewall
D. The firewall itself is blocking ports 21 through 23 and a service is listening on port 23 of the target host
QUESTION 9:
Why is a penetration test considered to be more thorough than a vulnerability scan?
A. Vulnerability scans only do host discovery and port scanning by default.
B. A penetration test actively exploits vulnerabilities in the targeted infrastructure, while a vulnerability scan does not typically involve active exploitation.
C. It is not ? a penetration test is often performed by an automated tool, while a vulnerability scan requires active engagement.
D. The tools used by penetration testers tend to have much more comprehensive vulnerability databases.
QUESTION 10:
What is the file that determines the basic configuration (specifically activities, services, broadcast receivers, etc.) in an Android application?
A. AndroidManifest.xml
B. APK.info
C. resources.asrc
D. classes.dex
QUESTION 11:
You are a penetration tester working to test the user awareness of the employees of the client xyz. You
harvested two employees\’ emails from some public sources and are creating a client-side backdoor to
send it to the employees via email.
Which stage of the cyber kill chain are you at?
A. Reconnaissance
B. Command and control
C. Weaponization
D. Exploitation
QUESTION 12:
Louis, a professional hacker, had used specialized tools or search engines to encrypt all his browsing activity and navigate anonymously to obtain sensitive/hidden information about official government or federal databases. After gathering the Information, he successfully performed an attack on the target government organization without being traced. Which of the following techniques is described in the above scenario?
A. Dark web footprinting
B. VoIP footpnnting
C. VPN footprinting
D. website footprinting
QUESTION 13:
Which of the following Google advanced search operators helps an attacker in gathering information about websites that are similar to a specified target URL?
A. [inurl:]
B. [related:]
C. [info:]
D. [site:]
Verify answer:
| Number: | Answers: | Illustrate: |
| Q1 | A | |
| Q2 | C | |
| Q3 | A | |
| Q4 | B | A white hat (or a white hat hacker) is an ethical computer hacker, or a computer security expert, who focuses on penetration testing and in other testing methodologies that ensures the safety of an organization\’s information systems. Ethical hacking may be a term meant to imply a broader category than simply penetration testing. Contrasted with black hat, a malicious hacker, the name comes from Western films, where heroic and antagonistic cowboys might traditionally wear a white and a black hat respectively. While a white hat hacker hacks under good intentions with permission, and a black hat hacker, most frequently unauthorized, has malicious intent, there\’s a 3rd kind referred to as a gray hat hacker who hacks with good intentions but sometimes without permission.White hat hackers can also add teams called “sneakers and/or hacker clubs”,red teams, or tiger teams.While penetration testing concentrates on attacking software and computer systems from the beginning ?scanning ports, examining known defects in protocols and applications running on the system and patch installations, as an example ?ethical hacking may include other things. A full-blown ethical hack might include emailing staff to invite password details, searching through executive\’s dustbins and typically breaking and entering, without the knowledge and consent of the targets. Only the owners, CEOs and Board Members (stake holders) who asked for such a censoring of this magnitude are aware. to undertake to duplicate a number of the destructive techniques a true attack might employ, ethical hackers may arrange for cloned test systems, or organize a hack late in the dark while systems are less critical. In most up-to-date cases these hacks perpetuate for the long-term con (days, if not weeks, of long-term human infiltration into an organization). Some examples include leaving USB/flash key drives with hidden auto-start software during a public area as if someone lost the tiny drive and an unsuspecting employee found it and took it.Some other methods of completing these include:?DoS attacks?Social engineering tactics?Reverse engineering? Network security?Disk and memory forensics?Vulnerability research?Security scanners such as:?W3af?Nessus?Burp suite? Frameworks such as:?Metasploit?Training PlatformsThese methods identify and exploit known security vulnerabilities and plan to evade security to realize entry into secured areas. they\’re ready to do that by hiding software and system back-doors\\’ which will be used as a link to information or access that a non-ethical hacker, also referred to asblack-hat\’ or `grey-hat\’, might want to succeed in Exam E |
| Q5 | B | |
| Q6 | A | |
| Q7 | D | |
| Q8 | C | |
| Q9 | B | |
| Q10 | A | The AndroidManifest.xml file contains information about your package, including components of the appliance like activities, services, broadcast receivers, content providers, etc. It performs other tasks also:?it\’s responsible to guard the appliance to access any protected parts by providing the permissions. It also declares the android API that the appliance goes to use. It lists the instrumentation classes. The instrumentation classes provide profiling and other information. This information is removed just before the appliance is published etc. This is the specified XML file for all the android applications and is located inside the basis directory. |
| Q11 | D | At this stage exploiting a vulnerability to execute code on the victim\’s direct channel for remote manipulation of the victim is the objective. Here ancient hardening measures add resiliency, however, custom defense capabilities are necessary to prevent zero-day exploits at this stage. once the weapon is delivered to the victim host, exploitation triggers intruders\’ code. Most often, exploitation targets Associate in the Nursing application or software vulnerability, however it may additionally additional merely exploit the users themselves or leverage Associate in Nursing software feature that auto- executes code. In recent years this has become a district of experience within the hacking community that is commonly incontestible at events like Blackhat, Defcon, and also the like. |
| Q12 | A | VoIP (Voice over Internet Protocol) is a web convention that permits the transmission of voice brings over the web. It does as such by changing over the ordinary telephone signals into advanced signs. Virtual Private Networks(VPN) give a protected association with an association \’ organization. Along these lines, VoIP traffic can disregard an SSL-based VPN, successfully scrambling VoIP administrations. When leading surveillance, in the underlying phases of VoIP footprinting, the accompanying freely accessible data can be normal: All open ports and administrations of the gadgets associated with the VoIP organization The public VoIP worker’s IP address The working arrangement of the worker running VoIP The organization framework |
| Q13 | B |
[Google Drive] Download the 312-50V11 dumps exam material above:https://drive.google.com/file/d/1IW-vsqqsN4-yp3ZoNmhIm42BJE6y58_m/
CEH v11 certification exam is really difficult, and certification exam questions are updated at each stage, so follow leads4pass and use 312-50V11 dumps updated throughout the year https://www.leads4pass.com/312-50v11.html Helping you pass the CEH v11 certification exam in no time.