Candidates use the latest updated CCNA 200-301 dumps from Lead4Pass: https://www.leads4pass.com/200-301.html, to help you get past the hurdle and successfully pass the 200-301 CCNA exam.
Lead4Pass 200-301 dumps provide PDF files and a VCE exam engine to help you practice 200-301 CCNA exam questions quickly and easily. The latest updated 200-301 dumps contain 294 exam questions and answers, verified by IT experts to be true and effective.
Share 13 CCNA 200-301 dumps PDF:https://drive.google.com/file/d/1hqDUcvc1vHJMiDa15KhDD1Jjp3q8j0hA/
Read CCNA 200-301 dumps exam questions and answers online:
| Number of exam questions | Release time | Exam name | From | Previous issue |
| 15 | Sep 20, 2022 | Implementing and Administering Cisco Solutions (CCNA) | Lead4Pass | Sep 2, 2022 |
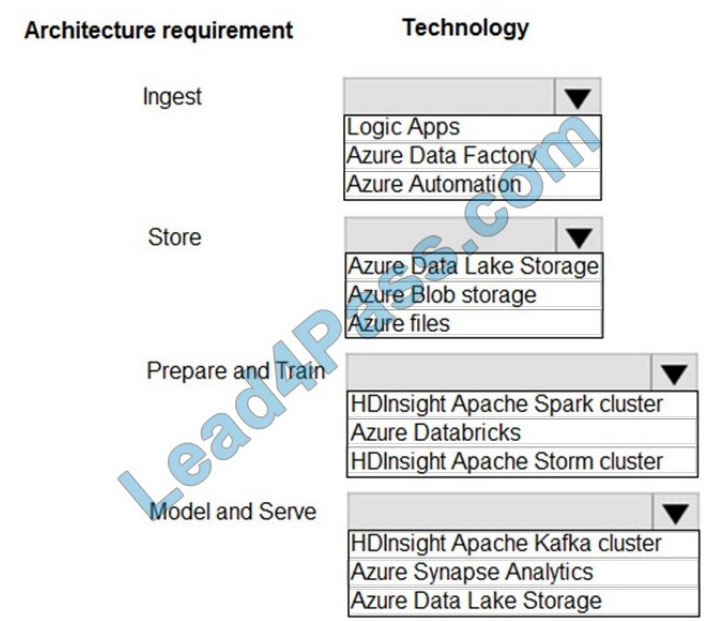
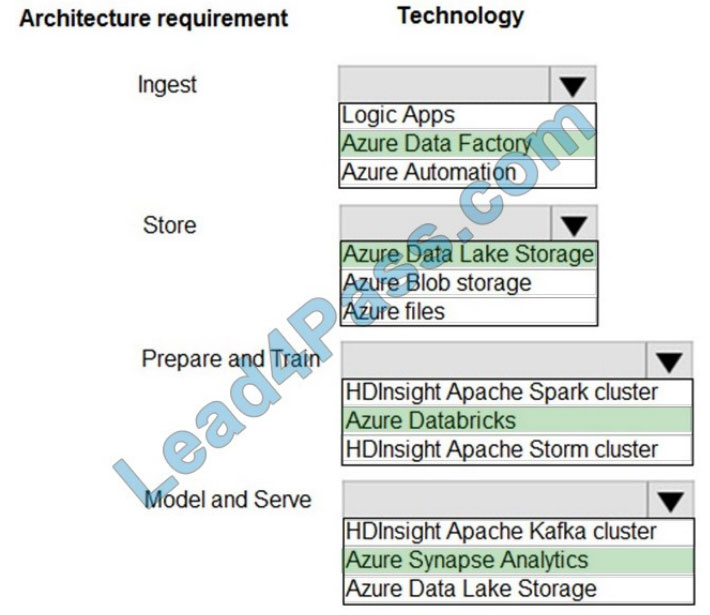
New Question 1:
DRAG DROP
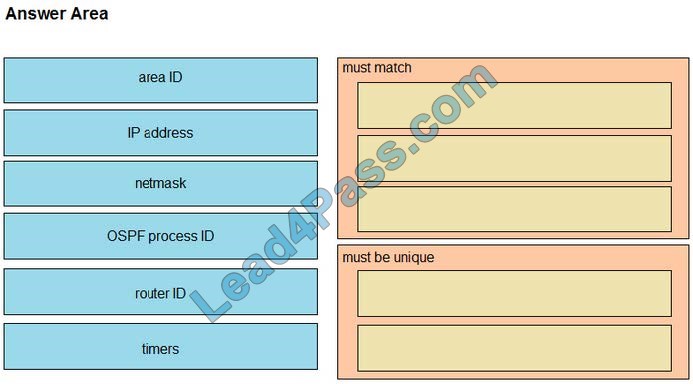
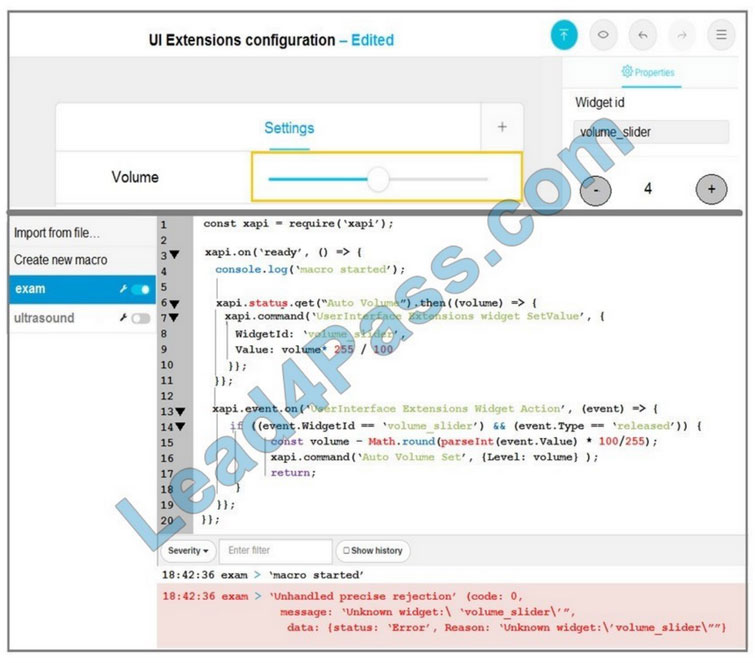
A network engineer is configuring an OSPFv2 neighbor adjacency. Drag and drop the parameters from the left onto their required categories on the right. Not all parameters are used.
Select and Place:
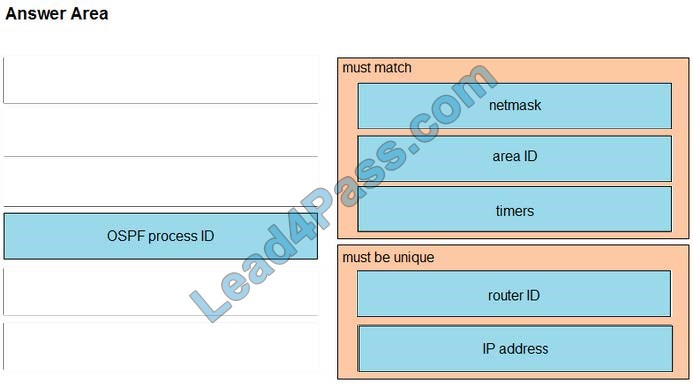
Correct Answer:
New Question 2:
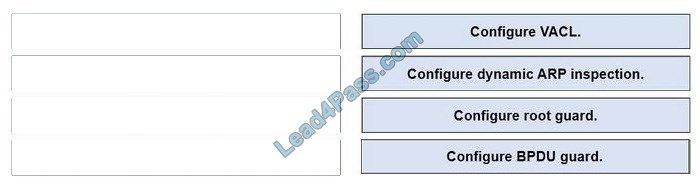
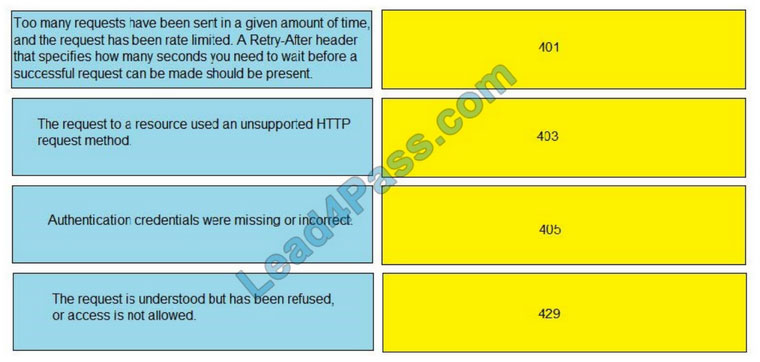
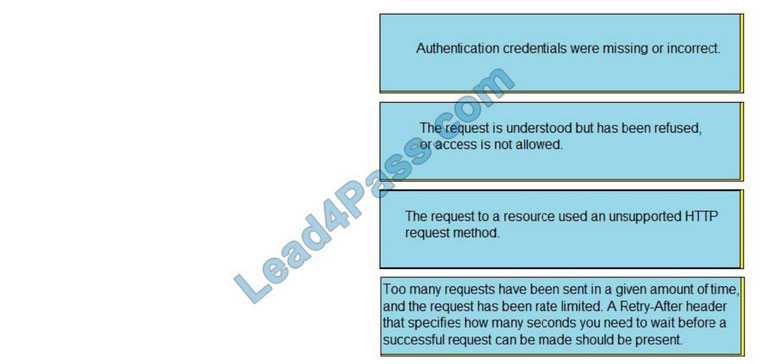
Drag and drop the threat-mitigation techniques from the left onto the types of threat or attack they mitigate on the right.
Select and Place:
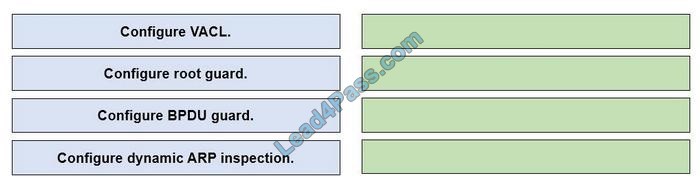
Correct Answer:
Double-Tagging attack:
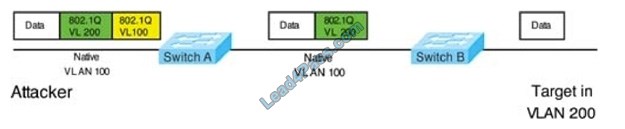
In this attack, the attacking computer generates frames with two 802.1Q tags. The first tag matches the native VLAN of the trunk port (VLAN 10 in this case), and the second matches the VLAN of a host it wants to attack (VLAN 20).
When the packet from the attacker reaches Switch A, Switch A only sees the first VLAN 10 and it matches with its native VLAN 10 so this VLAN tag is removed. Switch A forwards the frame out all links with the same native VLAN 10. Switch B
receives the frame with a tag of VLAN 20 so it removes this tag and forwards it out to the Victim’s computer.
Note: This attack only works if the trunk (between two switches) has the same native VLAN as the attacker.
To mitigate this type of attack, you can use VLAN access control lists (VACLs, which apply to all traffic within a VLAN. We can use VACL to drop attacker traffic to specific victims/servers) or implement Private VLANs.
ARP attack (like ARP poisoning/spoofing) is a type of attack in which a malicious actor sends falsified ARP messages over a local area network as ARP allows a gratuitous reply from a host even if an ARP request was not received. This
results in the linking of an attacker\’s MAC address with the IP address of a legitimate computer or server on the network. This is an attack based on ARP which is at Layer 2. Dynamic ARP inspection (DAI) is a security feature that validates ARP packets in a network which can be used to mitigate this type of attack.
New Question 3:
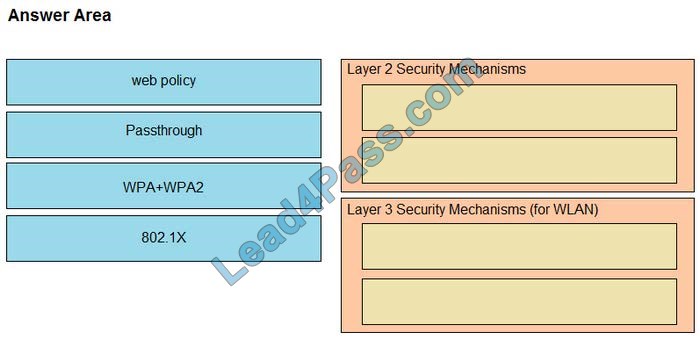
Drag and drop the Cisco Wireless LAN Controller security settings from the left onto the correct security mechanism categories on the right.
Select and Place:
Correct Answer:
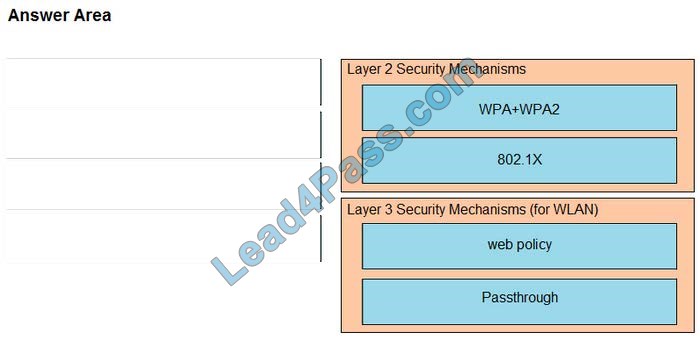
Layer 2 Security Mechanism includes WPA+WPA2, 802.1X, Static WEP, and CKIP while Layer 3 Security Mechanisms (for WLAN) includes IPSec, VPN Pass-Through, Web Passthrough …
New Question 4:
Drag and drop the network protocols from the left onto the correct transport services on the right.
Select and Place:
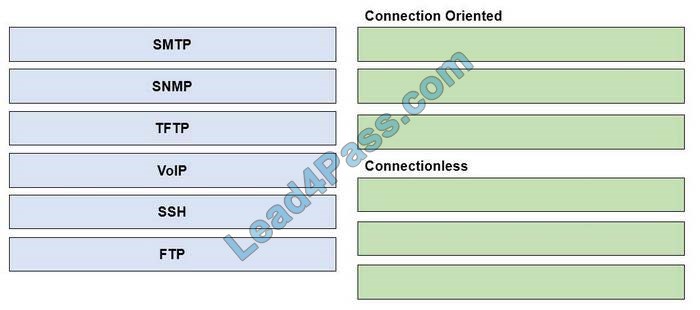
Correct Answer:
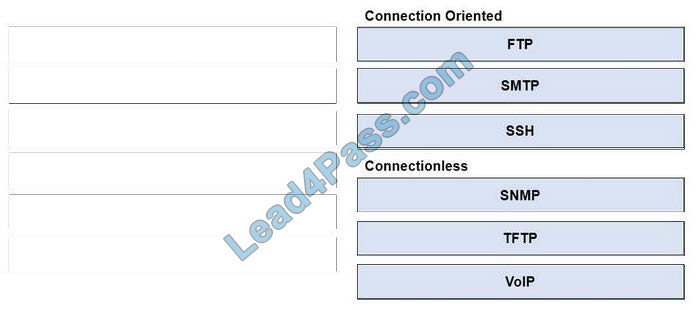
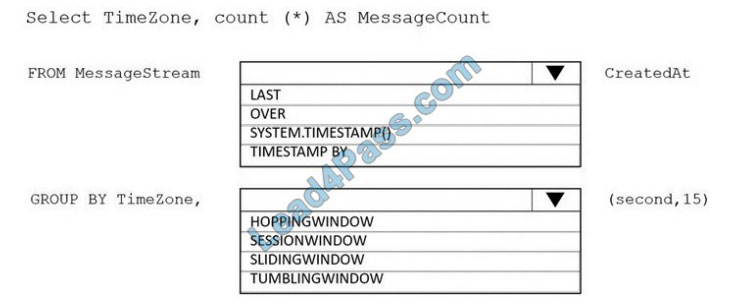
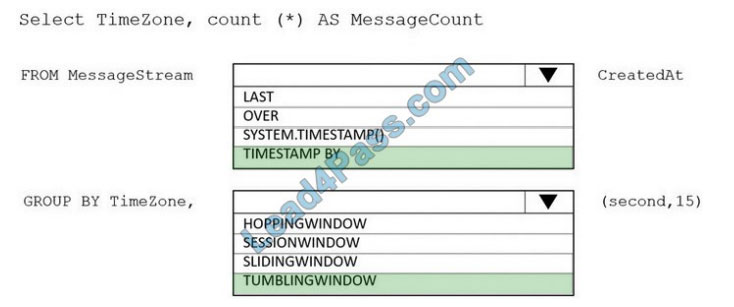
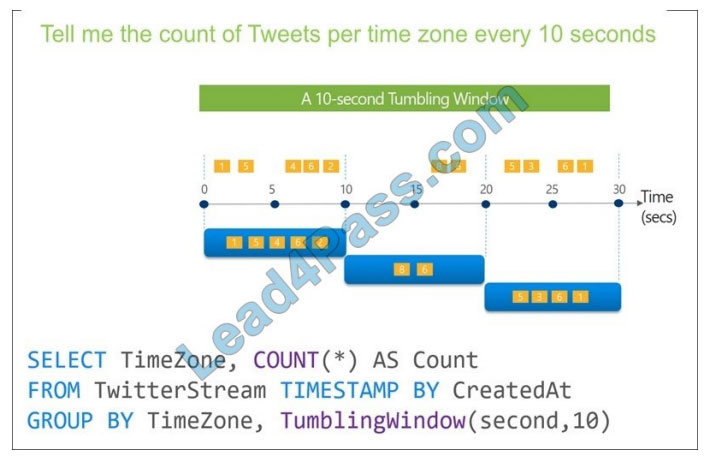
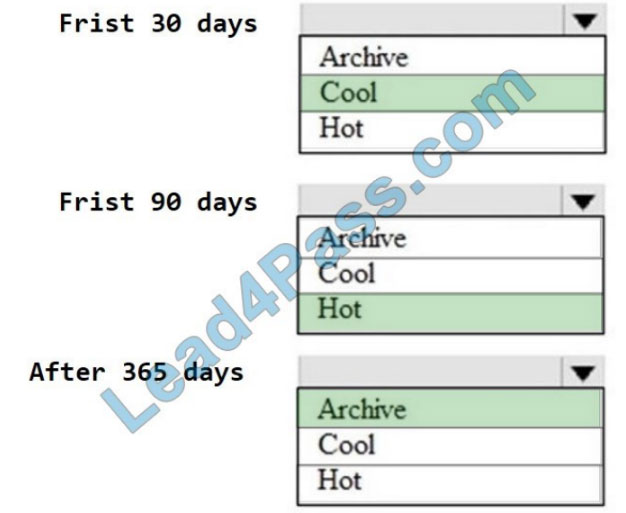
New Question 5:
DRAG DROP
Refer to the exhibit.
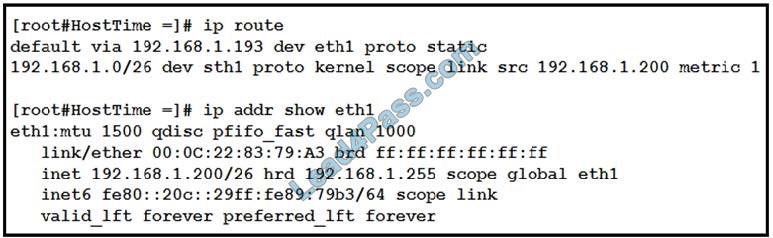
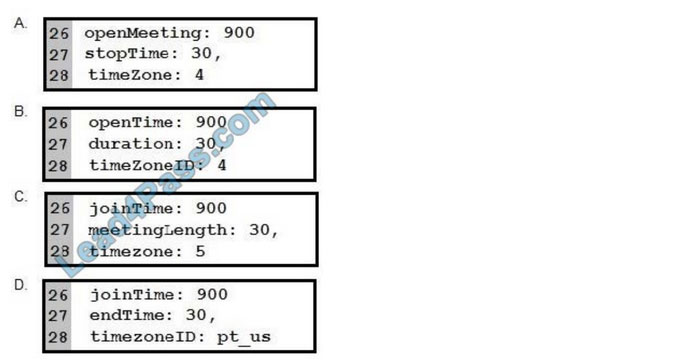
Drag and drop the networking parameters from the left onto the correct values on the right.
Select and Place:
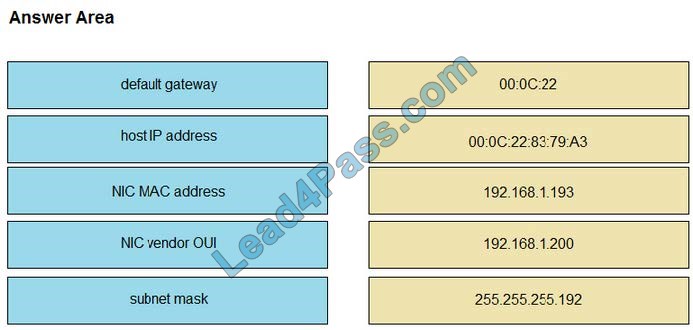
Correct Answer:
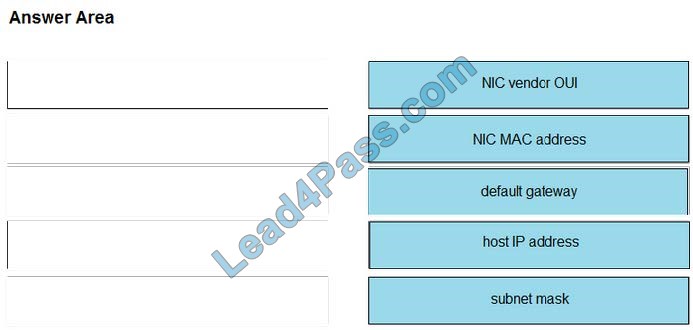
The “IP route” and “IP addr show eth1” are Linux commands.
1.
“IP route”: display the routing table
2.
“IP addr show eth1”: get depth information (only on eth1 interface) about your network interfaces like IP Address, MAC Address information
New Question 6:
DRAG DROP
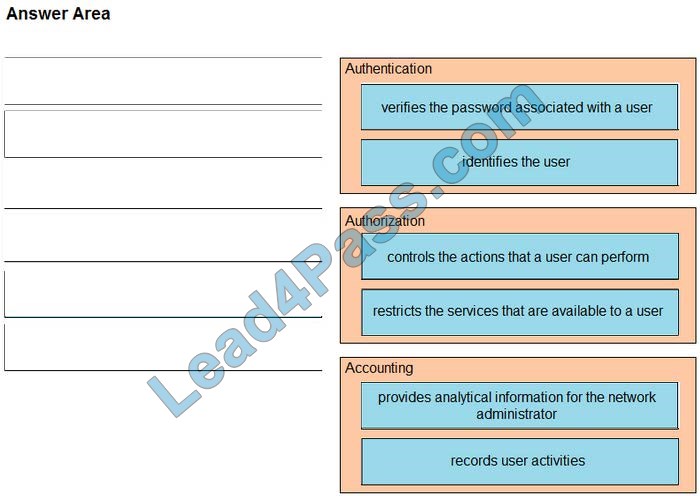
Drag and drop the AAA functions from the left onto the correct AAA services on the right.
Select and Place:
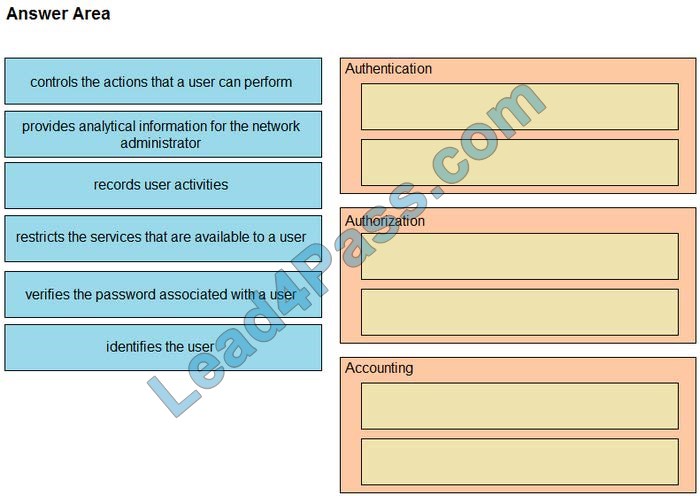
Correct Answer:
New Question 7:
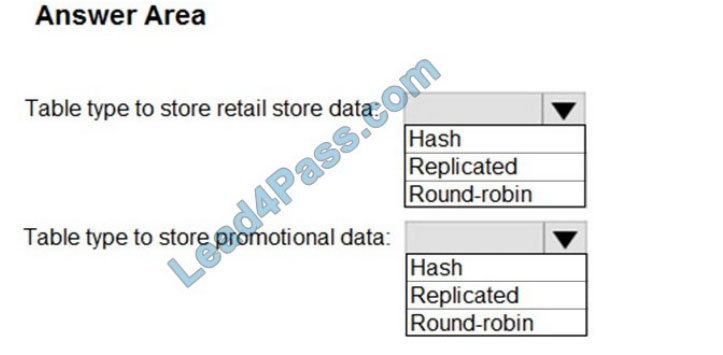
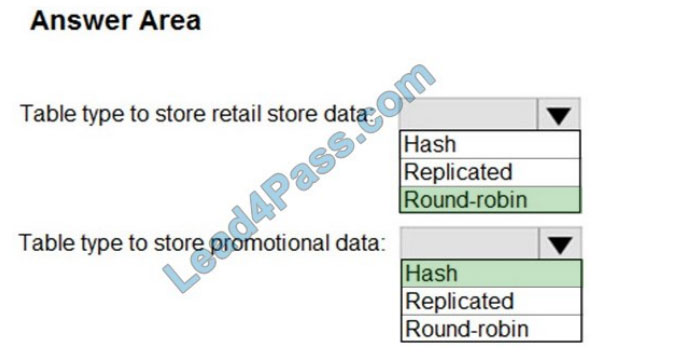
Drag and drop the IPv4 network subnets from the left onto the correct usable host ranges on the right.
Select and Place:
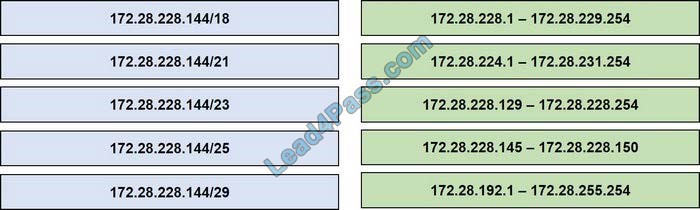
Correct Answer:
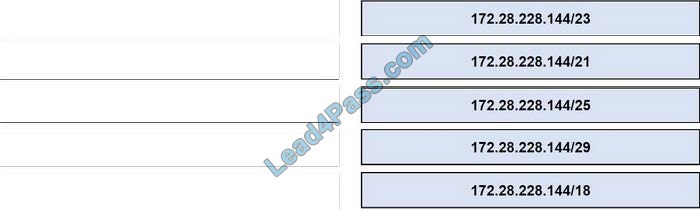
This subnet question requires us to grasp how to subnet very well. To quickly find out the subnet range, we have to find out the increment and the network address of each subnet. Let\’s take an example with the subnet 172.28.228.144/18:
From the /18 (= 1100 0000 in the 3rd octet), we find out the increment is 64. Therefore the network address of this subnet must be the greatest multiple of the increment but not greater than the value in the 3rd octet (228). We can find out the 3rd octet of the network address is 192 (because 192 = 64 * 3 and 192 < 228) -> The network address is 172.28.192.0. So the first usable host should be 172.28.192.1 and it matches with the 5th answer on the right. In this case, we don\’t need to calculate the broadcast address because we found the correct answer.
Let\’s take another example with subnet 172.28.228.144/23 -> The increment is 2 (as /23 = 1111 1110 in 3rd octet) -> The 3rd octet of the network address is 228 (because 228 is the multiply of 2 and equal to the 3rd octet) -> The network address is 172.28.228.0 -> The first usable host is 172.28.228.1. It is not necessary but if we want to find out the broadcast address of this subnet, we can find out the next network address, which is 172.28. (228 + the increment number).0 or
172.28.230.0 then reduce 1 bit -> 172.28.229.255 is the broadcast address of our subnet. Therefore the last usable host is 172.28.229.254.
New Question 8:
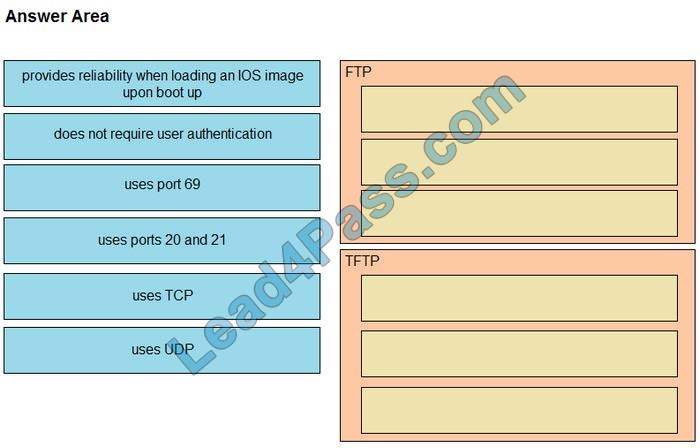
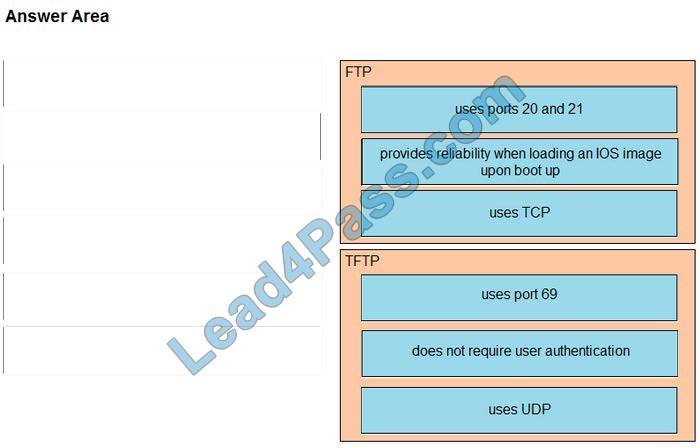
Drag and drop the descriptions of file-transfer protocols from the left onto the correct protocols on the right.
Select and Place:
Correct Answer:
New Question 9:
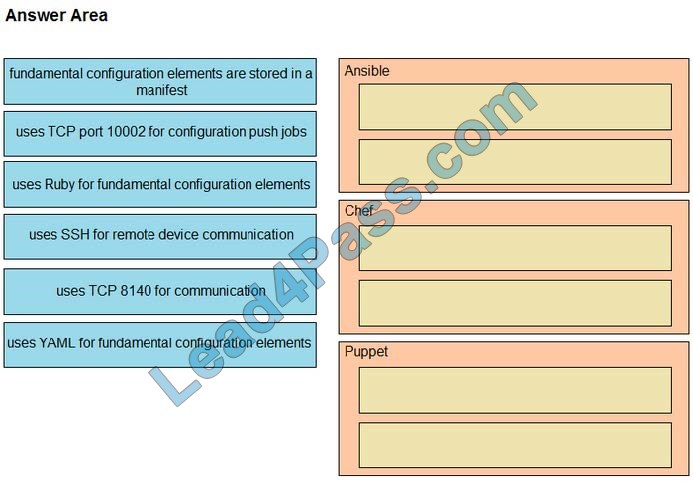
Drag-drop the descriptions from the left onto the correct configuration-management technologies on the right.
Select and Place:
Correct Answer:
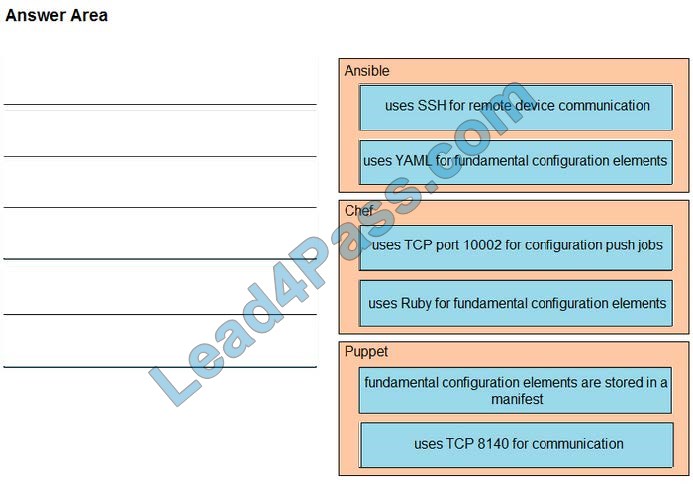
The focus of Ansible is to be streamlined and fast and to require no node agent installation. Thus, Ansible performs all functions over SSH. Ansible is built on Python, in contrast to the Ruby foundation of Puppet and Chef.
TCP port 10002 is the command port. It may be configured in the Chef Push Jobs configuration file. This port allows Chef Push Jobs clients to communicate with the Chef Push Jobs server.
Puppet is an open-source configuration management solution, which is built with Ruby and offers custom Domain Specific Language (DSL) and Embedded Ruby (ERB) templates to create custom Puppet language files, offering a declarative-
paradigm programming approach.
A Puppet piece of code is called a manifest and is a file with a .pp extension.
New Question 10:
Drag and drop the WLAN components from the left onto the correct descriptions on the right.
Select and Place:
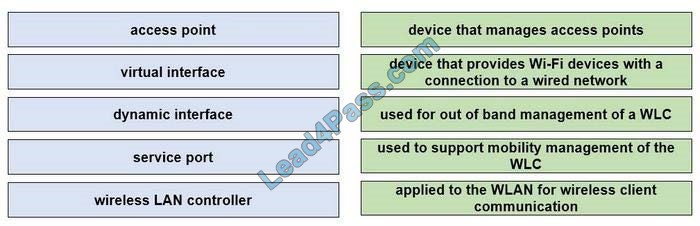
Correct Answer:
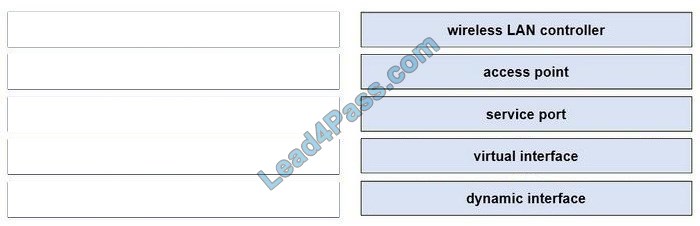
The service port can be used for management purposes, primarily for out-of-band management. However, AP management traffic is not possible across the service port. In most cases, the service port is used as a “last resort” means of accessing the controller GUI for management purposes. For example, in the case where the system distribution ports on the controller are down or their communication to the wired network is otherwise degraded.
A dynamic interface with the Dynamic AP Management option enabled is used as the tunnel source for packets from the controller to the access point and as the destination for CAPWAP packets from the access point to the controller. The virtual interface is used to support mobility management, Dynamic Host Configuration Protocol (DHCP) relay, and embedded Layer 3 security such as guest web authentication. It also maintains the DNS gateway hostname used by Layer 3 security and mobility managers to verify the source of certificates when Layer 3 web authorization is enabled.
New Question 11:
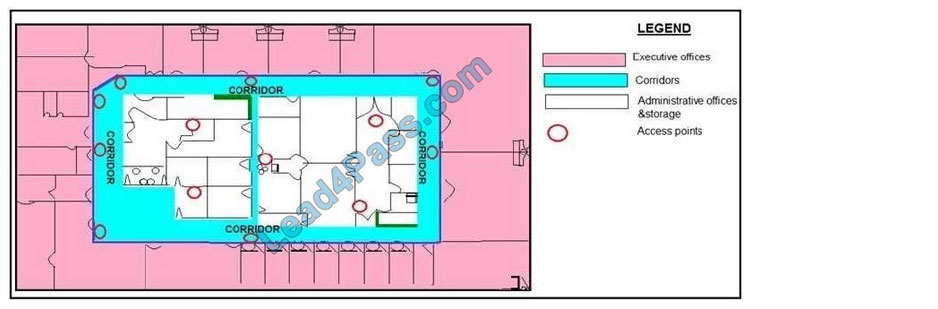
Drag and drop the functions from the left onto the correct network components on the right.
Select and Place:
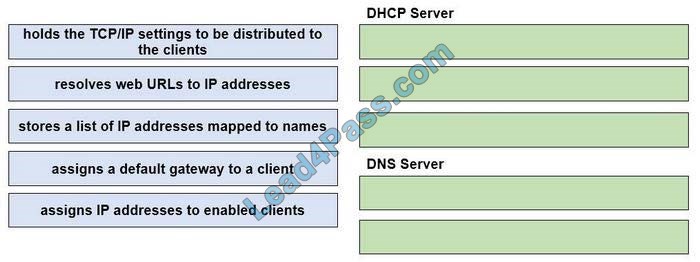
Correct Answer:
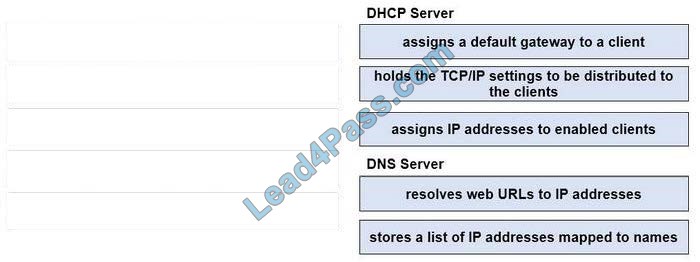
Refer to the exhibit.

New Question 12:
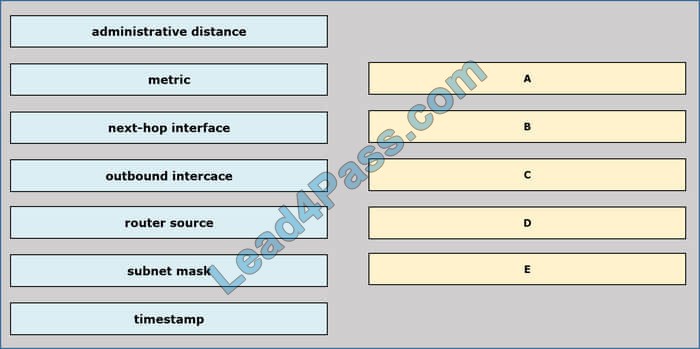
Drag and drop the routing table components on the left onto the corresponding letter from the exhibit on the right. not all options are used.
Select and Place:
Correct Answer:
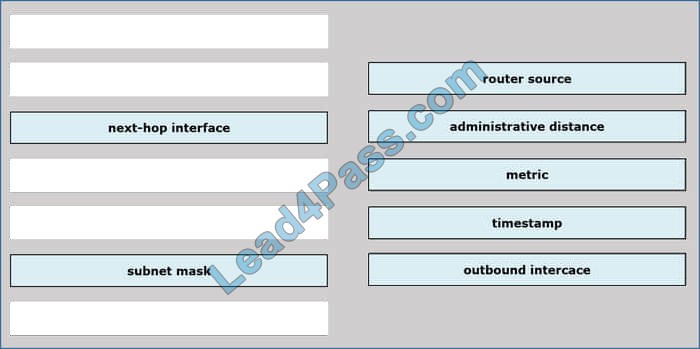
New Question 13:
Drag and drop each broadcast IP address on the left to the Broadcast Address column on the right. Not all options are used.
Select and Place:

Correct Answer:

New Question 14:
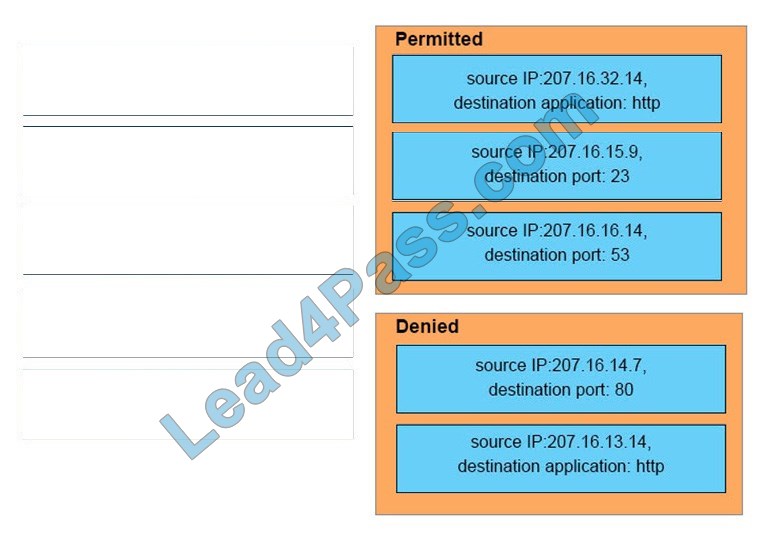
An interface has been configured with the access list that is shown below.
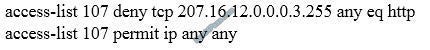
On the basis of that access list, drag each information packet on the left to the appropriate category on the right.
Select and Place:
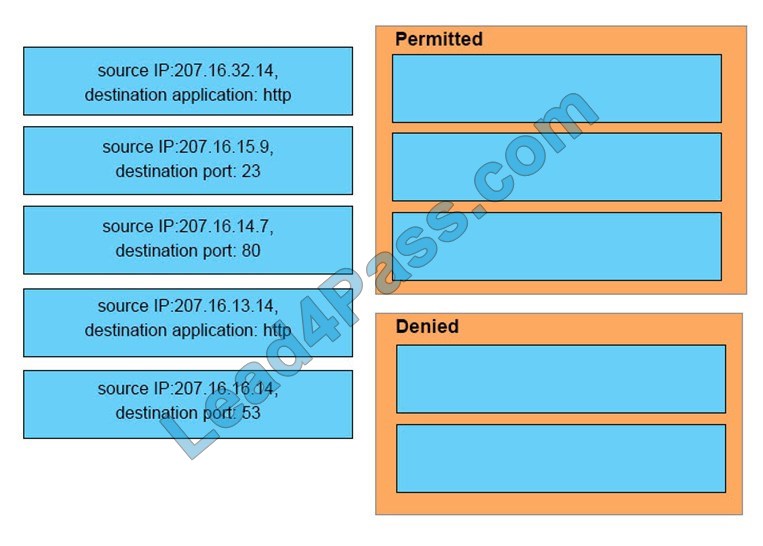
Correct Answer:
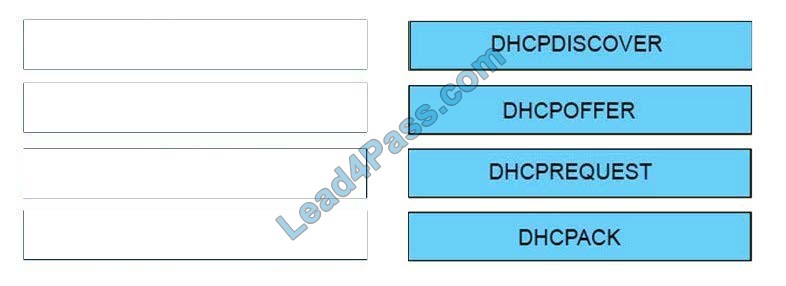
New Question 15:
Order the DHCP message types as they would occur between a DHCP client and a DHCP server.
Select and Place:
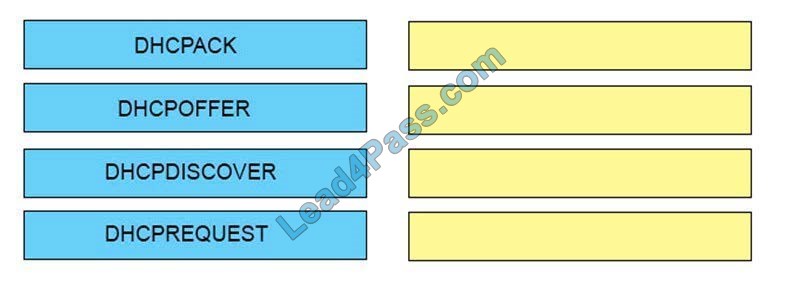
Correct Answer:
…
Download 13 CCNA 200-301 dumps PDF:https://drive.google.com/file/d/1hqDUcvc1vHJMiDa15KhDD1Jjp3q8j0hA/
Candidates studying the CCNA 200-301 dumps exam questions above can help them improve their exam experience, but this is only a warm-up.
You are welcome to download the latest updated CCNA 200-301 dumps: https://www.leads4pass.com/200-301.html, A truly effective route for candidates to pass the 200-301 CCNA exam.













![[2021.1] lead4pass md-100 exam questions q2](https://www.examineeverything.org/wp-content/uploads/2021/01/q2.jpg)
![[2021.1] lead4pass md-100 exam questions q2-1](https://www.examineeverything.org/wp-content/uploads/2021/01/q2-1.jpg)
![[2021.1] lead4pass md-100 exam questions q5](https://www.examineeverything.org/wp-content/uploads/2021/01/q5.jpg)
![[2021.1] lead4pass md-100 exam questions q6](https://www.examineeverything.org/wp-content/uploads/2021/01/q6.jpg)
![[2021.1] lead4pass md-100 exam questions q7](https://www.examineeverything.org/wp-content/uploads/2021/01/q7.jpg)
![[2021.1] lead4pass md-100 exam questions q7-1](https://www.examineeverything.org/wp-content/uploads/2021/01/q7-1.jpg)
![[2021.1] lead4pass md-100 exam questions q7-2](https://www.examineeverything.org/wp-content/uploads/2021/01/q7-2.jpg)
![[2021.1] lead4pass md-100 exam questions q10](https://www.examineeverything.org/wp-content/uploads/2021/01/q10.jpg)
![[2021.1] lead4pass md-100 exam questions q11](https://www.examineeverything.org/wp-content/uploads/2021/01/q11.jpg)
![[2021.1] lead4pass md-100 exam questions q11-1](https://www.examineeverything.org/wp-content/uploads/2021/01/q11-1.jpg)
![[2021.1] lead4pass md-100 exam questions q12](https://www.examineeverything.org/wp-content/uploads/2021/01/q12.jpg)
![[2021.1] lead4pass md-100 exam questions q13](https://www.examineeverything.org/wp-content/uploads/2021/01/q13.jpg)