
How do I successfully pass the EC-COUNCIL ECSA ECSAV10 exam?
Examineeverything updates EC-COUNCIL Free Exam Dumps Blog throughout the year! “EC-Council Network Security Administrator” ECSAV10 exam. You can find the free ECSAV10 pdf, ECSAV10 practice question online test, and our recommended https://www.leads4pass.com/ecsav10.html brand site in Examineeverything! Easy access to ECSAV10 exam dumps!
Examineeverything ECSAV10 exam catalog
- Latest EC-COUNCIL ECSAV10 youtube
- Latest EC-COUNCIL ECSAV10 google drive
- Latest EC-COUNCIL ECSAV10 Exam Practice
- Latest EC-COUNCIL ECSAV10 coupon code 2020
- leads4pass Reviews 2020
Latest EC-COUNCIL ECSAV10 exam pdf free download
[PDF Q1-Q13] Free EC-COUNCIL ECSAV10 pdf dumps download from Google Drive: https://drive.google.com/file/d/1HZOxERzGJVnO_SPSmYRuW5kwle063w91/
ECSA v10 – EC-Council: https://www.eccouncil.org/wp-content/uploads/2016/07/ECSAv10-Brochure.pdf
Latest Updates EC-COUNCIL ECSAV10 Exam Practice Questions and Answers
QUESTION 1
Identify the injection attack represented in the diagram below: A. XPath Injection Attack
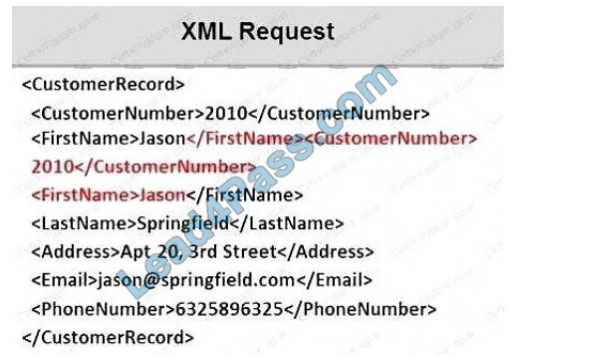
B. XML Request Attack
C. XML Injection Attack
D. Frame Injection Attack
Correct Answer: C
QUESTION 2
What are the scanning techniques that are used to bypass firewall rules and logging mechanisms and disguise
themselves as usual network traffic?
A. Connect Scanning Techniques
B. SYN Scanning Techniques
C. Stealth Scanning Techniques
D. Port Scanning Techniques
Correct Answer: C
QUESTION 3
Which of the following has an offset field that specifies the length of the header and data?
A. IP Header
B. UDP Header
C. ICMP Header
D. TCP Header
Correct Answer: D
QUESTION 4
Variables are used to define parameters for detection, specifically those of your local network and/or specific servers or
ports for inclusion or exclusion in rules. These are simple substitution variables set with the var keyword. Which one of
the following operators is used to define meta-variables?
A. “$”
B. “#”
C. “*”
D. “?”
Correct Answer: A
QUESTION 5
ARP spoofing is a technique whereby an attacker sends fake (“spoofed”) Address Resolution Protocol (ARP) messages
onto a Local Area Network. Generally, the aim is to associate the attacker\’s MAC address with the IP address of
another
host (such as the default gateway), causing any traffic meant for that IP address to be sent to the attacker instead.
ARP spoofing attack is used as an opening for other attacks.
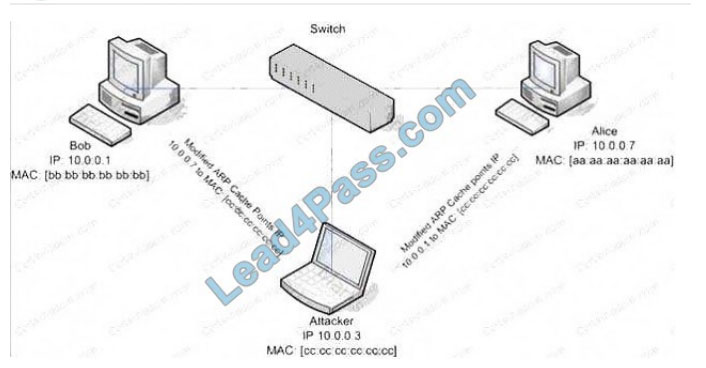
What type of attack would you launch after successfully deploying ARP spoofing?
A. Parameter Filtering
B. Social Engineering
C. Input Validation
D. Session Hijacking
Correct Answer: D
QUESTION 6
TCP/IP provides a broad range of communication protocols for the various applications on the network. The TCP/IP
model has four layers with major protocols included within each layer. Which one of the following protocols is used to
collect information from all the network devices?
A. Simple Network Management Protocol (SNMP)
B. Network File system (NFS)
C. Internet Control Message Protocol (ICMP)
D. Transmission Control Protocol (TCP)
Correct Answer: A
QUESTION 7
Harold is a web designer who has completed a website for ghttech.net. As part of the maintenance agreement he
signed with the client, Harold is performing research online and seeing how much exposure the site has received so far.
Harold
navigates to google.com and types in the following search.
link:www.ghttech.net
What will this search produce?
A. All sites that link to ghttech.net
B. Sites that contain the code: link:www.ghttech.net
C. All sites that ghttech.net links to
D. All search engines that link to .net domains
Correct Answer: A
QUESTION 8
Metasploit framework is an open-source platform for vulnerability research, development, and penetration testing. Which
one of the following Metasploit options is used to exploit multiple systems at once?
A. NinjaDontKill
B. NinjaHost
C. RandomNops
D. EnablePython
Correct Answer: A
QUESTION 9
One needs to run the “Scan Server Configuration” tool to allow a remote connection to Nessus from the remote Nessus
clients. This tool allows the port and bound interface of the Nessus daemon to be configured. By default, the Nessus
daemon listens to connections on which one of the following?
A. Localhost (127.0.0.1) and port 1241
B. Localhost (127.0.0.1) and port 1240
C. Localhost (127.0.0.1) and port 1246
D. Localhost (127.0.0.0) and port 1243
Correct Answer: A
QUESTION 10
Which of the following methods is used to perform server discovery?
A. Banner Grabbing
B. Who is Lookup
C. SQL Injection
D. Session Hijacking
Correct Answer: B
QUESTION 11
In Linux, what is the smallest possible shellcode?
A. 800 bytes
B. 8 bytes
C. 80 bytes
D. 24 bytes
Correct Answer: D
QUESTION 12
A firewall protects networked computers from intentional hostile intrusion that could compromise confidentiality or result
in data corruption or denial of service. It examines all traffic routed between the two networks to see if it meets certain
criteria; If it does, it is routed between the networks, otherwise, it is stopped.
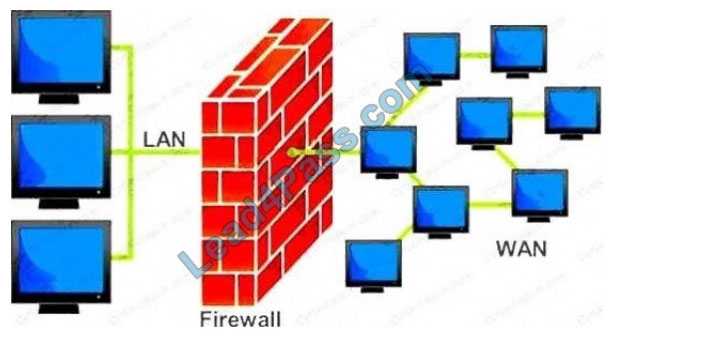
Why is an appliance-based firewall is more secure than those implemented on top of the commercial operating system
(Software based)?
A. Appliance based firewalls cannot be upgraded
B. Firewalls implemented on a hardware firewall are highly scalable
C. Hardware appliances do not suffer from security vulnerabilities associated with the underlying operating system
D. Operating system firewalls are highly configured
Correct Answer: A
Share lead4Pass EC-COUNCIL ECSAV10 Discount codes for free 2020

leads4pass Reviews
leads4pass has about 10 years of exam experience! Helped many friends pass the EC-COUNCIL exam! leads4pass Year-round Update Exam guarantees up-to-date and effective! Highest pass rate! The highest price/performance ratio! Guaranteed first attempt to pass the exam!
EC-COUNCIL ECSAV10 Exam Tips Summary:
EC-COUNCIL ECSAV10 is already the ultimate help here, we share the latest exam pdf, the latest online exercise questions!
And the brand website recommends “leads4pass”.
Latest update leads4pass ECSAV10 exam dumps: https://www.leads4pass.com/ecsav10.html (204 Q&As)
[Q1-Q12 PDF] Free EC-COUNCIL ECSAV10 pdf dumps download from Google Drive: https://drive.google.com/file/d/1HZOxERzGJVnO_SPSmYRuW5kwle063w91/