How do I successfully pass the EC-COUNCIL Certified Ethical Hacker 312-38 exam? Examineeverything updates EC-COUNCIL Free Exam Dumps Blog throughout the year! “EC-Council Network Security Administrator” 312-38 exam. You can find the free 312-38 pdf, 312-38 practice question online test, and our recommended https://www.leads4pass.com/312-38.html brand site in Examineeverything! Easy access to 312-38 exam dumps!
Examineeverything 312-38 exam catalog
- Latest EC-COUNCIL 312-38 youtube
- Latest EC-COUNCIL 312-38 google drive
- Latest EC-COUNCIL 312-38 Exam Practice
- Latest EC-COUNCIL 312-38 coupon code 2020
- Lead4Pass Reviews 2020
Latest EC-COUNCIL 312-38 exam pdf free download
[PDF Q1-Q13] Free EC-COUNCIL 312-38 pdf dumps download from Google Drive: https://drive.google.com/file/d/1S9b7nZx9IGVcfMEOLqAm3IFVsBE39af2
Certified Network Defender – CND | EC-Council: https://www.eccouncil.org/programs/certified-network-defender-cnd/
Latest Updates EC-COUNCIL 312-38 Exam Practice Questions and Answers
QUESTION 1
Fill in the blank with the appropriate term. is an open wireless technology standard for exchanging data over short
distances from fixed and mobile devices.
Correct Answer: Bluetooth
Bluetooth is an open wireless technology standard for exchanging data over short distances from fixed and mobile
devices,
creating personal area networks with high levels of security. Created by telecoms vendor Ericsson in 1994, it was
originally conceived as a wireless alternative to RS-232 data cables. It can connect several devices, overcoming
problems of
synchronization. Today Bluetooth is managed by the Bluetooth Special Interest Group.
QUESTION 2
Which of the following is a passive attack?
A. Unauthorized access
B. Traffic analysis
C. Replay attack
D. Session hijacking
Correct Answer: B
QUESTION 3
Which of the following layers of the OSI model provides interhost communication?
A. Application layer
B. Network layer
C. Transport layer
D. Session layer
Correct Answer: D
QUESTION 4
Jason works as a System Administrator for www.company.com Inc. The company has a Windows-based network. Sam,
an employee of the company, accidentally changes some of the applications and system settings. He complains to
Jason that his system is not working properly. To troubleshoot the problem, Jason diagnoses the internals of his
computer and observes that some changes have been made in Sam\’s computer registry. To rectify the issue, Jason
has to restore the registry. Which of the following utilities can Jason use to accomplish the task? Each correct answer
represents a complete solution. Choose all that apply.
A. Reg.exe
B. EventCombMT
C. Regedit.exe
D. Resplendent registrar
Correct Answer: ACD
A resplendent registrar is a tool that offers a complete and safe solution to administrators and power users for
maintaining the registry. It can be used for maintaining the registry of desktops and remote computers on the network. It
offers a solution for backing up and restoring registries, fast background search and replace, adding descriptions to the
registry keys, etc. This program is very attractive and easy to use, as it comes in an explorer-style interface. It can be
used for Windows 2003/XP/2K/NT/ME/9x. Reg.exe is a command-line utility that is used to edit the Windows registry. It
has the ability to import, export, back up, and restore keys, as well as to compare, modify, and delete keys. It can
perform almost all tasks that can be done using the Windows-based Regedit.exe tool. Registry Editor (REGEDIT) is a
registry editing utility that can be used to look at the information in the registry. REGEDIT.EXE enables users to search for
strings, values, keys, and subkeys and is useful to find a specific value or string. Users can also use REGEDIT.EXE to
add, delete, or modify registry entries. Answer option B is incorrect. EventCombMT is a multithreaded tool that is used
to search the event logs of several different computers for specific events, all from one central location. It is a little-known Microsoft tool to run searches for event IDs or text strings against Windows event logs for systems, applications,
and security, as well as File Replication Service (FRS), domain name system (DNS), and Active Directory (AD) logs
where applicable. The MT stands for multi-threaded. The program is part of the Account Lockout and Management
The tools program package for Windows 2000, 2003, and XP.
QUESTION 5
Which of the following is the primary international body for fostering cooperative standards for telecommunications
equipment and systems?
A. ICANN
B. IEEE
C. NIST
D. CCITT
Correct Answer: D
CCITT is the primary international body for fostering cooperative standards for telecommunications equipment and
systems. It is now known as the ITU-T (for Telecommunication Standardization Sector of the International
Telecommunications Union). The ITU-T mission is to ensure the efficient and timely production of standards covering all
fields of telecommunications on a worldwide basis, as well as defining tariff and accounting principles for international
telecommunication services. Answer option A is incorrect. Internet Corporation for Assigned Names and Numbers
(ICANN) is a non-profit organization that oversees the allocation of IP addresses, management of the DNS
infrastructure, protocol parameter assignment, and root server system management. Answer option B is incorrect. The
Institute of Electrical and Electronics Engineers (IEEE) is a society of technical professionals. It promotes the
development and application of electro-technology and allied sciences. IEEE develops communications and network
standards, among other activities. The organization publishes a number of journals, has many local chapters, and
societies in specialized areas. Answer option C is incorrect. The National Institute of Standards and Technology (NIST),
known between 1901 and 1988 as the National Bureau of Standards (NBS), is a measurement standards laboratory
which is a non-regulatory agency of the United States Department of Commerce. The institute\’s official mission is as
follows: To promote U.S. innovation and industrial competitiveness by advancing measurement science, standards, and
technology in ways that enhance economic security and improve quality of life. NIST had an operating budget for the fiscal
year 2007 (October 1, 2006-September 30, 2007) of about $843.3 million. NIST\’s 2009 budget was $992 million, but it
also received $610 million as part of the American Recovery and Reinvestment Act. NIST employs about 2,900
scientists, engineers, technicians, and support and administrative personnel. About 1,800 NIST associates (guest
researchers and engineers from American companies and foreign nations) complement the staff. In addition, NIST
partners with 1,400 manufacturing specialists and staff at nearly 350 affiliated centers around the country.
QUESTION 6
Which of the following statements are true about an IPv6 network? Each correct answer represents a complete solution.
Choose all that apply.
A. For interoperability, IPv4 addresses use the last 32 bits of IPv6 addresses.
B. It increases the number of available IP addresses.
C. It uses longer subnet masks than those used in IPv4.
D. It provides improved authentication and security.
E. It uses 128-bit addresses.
Correct Answer: BEAD
IP addressing version 6 (IPv6) is the latest version of IP addresses. IPv6 is designed to solve many of the problems
that were faced by IPv4, such as address depletion, security, auto-configuration, and extensibility. With the fast
increasing number of networks and the expansion of the World Wide Web, the allotted IP addresses are depleting rapidly, and the
need for more network addresses is arising. IPv6 solves this problem, as it uses a 128-bit address that can produce a
lot
more IP addresses. These addresses are hexadecimal numbers, made up of eight octet pairs. An example of an IPv6
address is 45CF: 6D53: 12CD: AFC7: E654: BB32: 543C: FACE.
Answer option C is incorrect. The subnet masks used in IPv6 addresses are of the same length as those used in IPv4
addresses.
QUESTION 7
Which of the following attacks comes under the category of an active attack?
A. Replay attack
B. Wireless footprinting
C. Passive Eavesdropping
D. Traffic analysis
Correct Answer: A
QUESTION 8
You work as the network administrator for uCertify Inc. The company has planned to add the support for IPv6
addressing. The initial phase deployment of IPv6 requires support from some IPv6-only devices. These devices need to
access servers that support only IPv4. Which of the following tools would be suitable to use?
A. Multipoint tunnels
B. NAT-PT
C. Point-to-point tunnels
D. Native IPv6
Correct Answer: B
NAT-PT (Network address translation-Protocol Translation) is useful when an IPv4-only host needs to communicate
with an IPv4-only host. NAT-PT (Network Address Translation-Protocol Translation) is an implementation of RFC 2766
as specified by the IETF. NAT-PT was designed so that it can be run on low-end, commodity hardware. NAT-PT runs in
user space, capturing and translating packets between the IPv6 and IPv4 networks (and vice-versa). NAT-PT uses the
Address Resolution Protocol (ARP) and Neighbor Discovery (ND) on the IPv4 and IPv6 network systems, respectively.
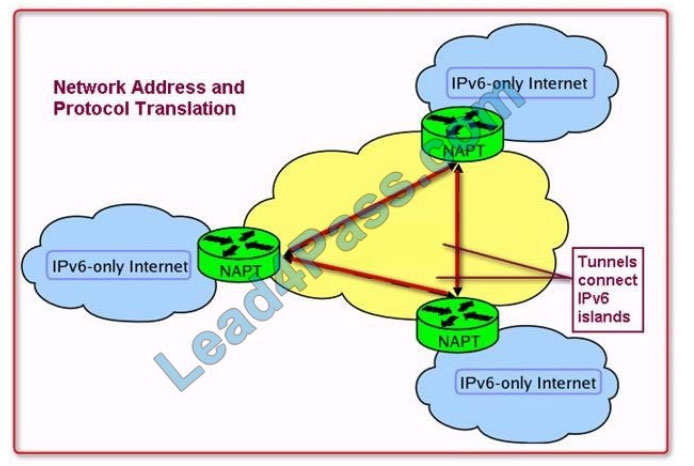
NAT-Protocol Translation can be used to translate both the source and destination IP addresses.
Answer option D is incorrect. Native IPv6 is of use when the IPv6 deployment is pervasive, with heavy traffic loads.
Answer option C is incorrect. Point-to-point tunnels work well when IPv6 is needed only in a subset of sites. These point-to-point tunnels act as a virtual point-to-point serial link. These are useful when the traffic is of very high volume. Answer
option A is incorrect. The multipoint tunnels are used for IPv6 deployment even when IPv6 is needed in a subset of sites
and is suitable when the traffic is infrequent and of less predictable volume.
QUESTION 9
Which of the following TCP/IP state transitions represents no connection state at all?
A. Closed
B. Closing
C. Close-wait
D. Fin-wait-1
Correct Answer: A
QUESTION 10
Which of the following is a worldwide organization that aims to establish, refine, and promote Internet security
standards?
A. ANSI
B. WASC
C. IEEE
D. ITU
Correct Answer: B
Web Application Security Consortium (WASC) is a worldwide organization that aims to establish, refine, and promote
Internet security standards. WASC is vendor-neutral, although members may belong to corporations involved in the
research, development, design, and distribution of Web security-related products.
Answer option A is incorrect. ANSI (American National Standards Institute) is the primary organization for fostering the
development of technology standards in the United States. ANSI works with industry groups and is the U.S. member of
the
International Organization for Standardization (ISO) and the International Electro-technical Commission (IEC). Long-established computer standards from ANSI include the American Standard Code for Information Interchange (ASCII)
and the
Small Computer System Interface (SCSI).
Answer option D is incorrect. The International Telecommunication Union (ITU) is an organization established to
standardize and regulate international radio and telecommunications. Its main tasks include standardization, allocation
of the
radio spectrum, and organizing interconnection arrangements between different countries to allow international phone
calls. ITU sets standards for global telecom networks. ITU\’s telecommunications division (ITU-T) produces more
than
200 standard recommendations each year in the converging areas of telecommunications, information technology,
consumer electronics, broadcasting, and multimedia communications. ITU was streamlined into the following three
sectors:
ITU-D (Telecommunication Development)
ITU-R (Radiocommunication)
ITU-T (Telecommunication Standardization)
Answer option C is incorrect. The Institute of Electrical and Electronics Engineers (IEEE) is a society of technical
professionals. It promotes the development and application of electro-technology and allied sciences. IEEE develops
communications and network standards, among other activities. The organization publishes a number of journals, has
many local chapters, and societies in specialized areas.
QUESTION 11
Which of the following is a management process that provides a framework to stimulate a rapid recovery, and the ability
to react effectively to protect the interests of its brand, reputation, and stakeholders?
A. None
B. log analysis
C. Business Continuity Management
D. patch management
E. response systems
Correct Answer: C
QUESTION 12
In an Ethernet peer-to-peer network, which of the following cables is used to connect two computers, using RJ-45
connectors and Category-5 UTP cable?
A. Serial
B. Loopback
C. Crossover
D. Parallel
Correct Answer: C
In an Ethernet peer-to-peer network, a crossover cable is used to connect two computers, using RJ-45 connectors and
Category-5 UTP cable. Answer options D and A are incorrect. Parallel and serial cables do not use RJ-45 connectors
and
Category-5 UTP cable. Parallel cables are used to connect printers, scanners etc., to computers, whereas serial cables
are used to connect modems, digital cameras etc., to computers.
Answer option B is incorrect. A loopback cable is used for testing equipments.
Share lead4Pass EC-COUNCIL 312-38 Discount codes for free 2020

Lead4Pass Reviews
Lead4Pass has about 10 years of exam experience! Helped many friends pass the EC-COUNCIL exam! Lead4pass Year-round Update Exam guarantees up-to-date and effective! Highest pass rate! The highest price/performance ratio! Guaranteed first attempt to pass the exam!
EC-COUNCIL 312-38 Exam Tips Summary:
EC-COUNCIL 312-38 is already the ultimate help here, we share the latest exam pdf, the latest online exercise questions!
And the brand website recommends “Lead4Pass”.
Latest update Lead4pass 312-38 exam dumps: https://www.leads4pass.com/312-38.html (382 Q&As)
[Q1-Q12 PDF] Free EC-COUNCIL 312-38 pdf dumps download from Google Drive: https://drive.google.com/file/d/1S9b7nZx9IGVcfMEOLqAm3IFVsBE39af2/